« Previous 1 2 3 4 Next »
Distributed denial of service attacks from and against the cloud
Cloud Wars
Application-Level DDoS
Recently, DDoS attacks have increasingly targeted very specific, well-documented vulnerabilities in certain services; this approach is known as DDoS at the application level (the seventh level in the OSI Reference Model; Figure 2). Attackers basically use the same approach as the Slow Read attack on the Apache web server, wherein Apache opens a new thread for each connection and maintains it for the duration of the communication. Attackers take advantage of this behavior by feeding Apache carefully metered data packets extremely slowly and simultaneously from as many sources as possible.
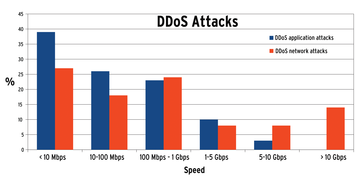 Figure 2: Data volumes of typical DDoS attacks against network resources (red) and server applications (blue).
Figure 2: Data volumes of typical DDoS attacks against network resources (red) and server applications (blue).
This approach is the easiest way to exploit Apache's capacity. According to Gartner researchers, about a quarter of all DDoS attacks in 2013 will target the application layer [5].
DDoS via HTTP
The defense against ACK reflection and SYN flood attacks relies on the same principle, regardless of whether the attacker uses HTTP or HTTPS. However, this is no longer true of application-level DDoS attacks. Sadly, the solutions designed to mitigate the effects of DDoS attacks are only capable of preventing DDoS via HTTP.
Data transferred via HTTPS are encrypted on their path through the Internet via firewalls, routers, and other computers up to the load balancer and finally to the web server. The cloud provider's DDoS protection measures and even the victim's defense mechanisms are completely ineffective if the data packets are encrypted.
Using WordPress in the DDoS Botnet
A new trend started to emerge in 2012: Perpetrators are increasingly gaining control not over desktop PCs but over high-performance servers in the cloud for performing carefully orchestrated DDoS attacks. In the DDoS attacks on US financial institutions last year, the offenders achieved 20 times the effect of ordinary desktop botnets with a handful of servers.
This trend exacerbated brute force attacks on WordPress sites in the cloud. A botnet with about 90,000 IP addresses bombards the popular CMS system with username-password combinations, giving the perpetrators time to gain access to its upload capabilities. The attackers then install their scripts and set up a back door to integrate the respective web server permanently into their existing botnet.
The problem of increasing prevalence of DDoS attacks is particularly severe for corporations with a scalable infrastructure. A few years ago, outsourcing some of the load to the cloud was common practice when facing a DDoS attack, to take advantage of the elastic scalability of the cloud. Meanwhile, however, the attack methods have become so sophisticated that the biggest advantage of the cloud, namely its scalability, can be fatal for the victim.
« Previous 1 2 3 4 Next »
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.




