« Previous 1 2 3 Next »
Mobile device management with Microsoft System Center 2012 R2
Professional Cleanup
Client Certificates
Depending on which platform you are using, the most complex process now starts before you can finally manage mobile endpoints with Windows Intune and SCC (Figure 2). For the iOS platform you need to request an Apple Push Notification certificate from Apple; for Windows Phone 8 you need to purchase a code signature certificate from Verisign. Windows Tablets with RT and RT 8.1 and Windows 8.1 devices that do not belong to the domain require a sideload key if you want access to apps other than those in the Windows App Store and if you want to set up your own app store.
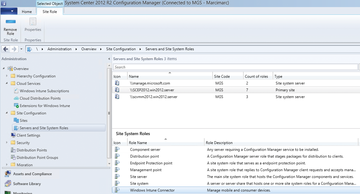 Figure 2: After completing the install, the Windows Intune Connector is available in the SCCM management console.
Figure 2: After completing the install, the Windows Intune Connector is available in the SCCM management console.
Companies with an Enterprise Software license can acquire a sideload key, and Microsoft recently loosened the requirements and restrictions for getting one. Administrators still need to note that all apps transferred by means of a sideload must be digitally signed. You can use public signature certificates or your internal public key infrastructure for this. Fortunately, you don't need to fulfill any additional requirements to manage Android devices [6].
After successfully setting up the Intune subscription and fulfilling all the requirements for Intune/SCCM integration, you can now start configuring System Center 2012 SP1 or newer (Figure 3). In the SCCM management console, you first need to add the Windows Intune Subscription to the Administration | Cloud Services node and log in to the Intune Portal with your Intune enterprise account. Later in the Intune integration wizard sequence, you will be prompted to state which mobile endpoint platforms you want to support. The choices are Windows Phone 8.0/8.1, Windows RT/8.1, Android, and Apple iOS.
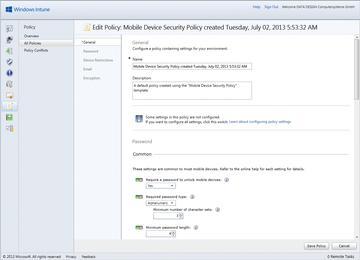 Figure 3: Following Intune integration, administrators can configure policies for mobile endpoints in System Center.
Figure 3: Following Intune integration, administrators can configure policies for mobile endpoints in System Center.
SCCM uses "Collections" of users and devices as the basis for distributing software and other SCCM activities. At this point, it makes sense to add all device owners activated in Windows Intune as the userbase for a new user Collection in SCCM. The Windows Intune Connector then uses this Collection as an additional authorization mechanism for users who will be able to roll out mobile devices in Intune. In additional subscription configuration steps, you can modify the look and feel of the Intune enterprise portal, adding, for example, your company logo and contact information.
Installing the Intune Connector
After setting up the Windows Intune subscription in the SCCM management console, your next step is to install the Windows Intune Connector Site System role. SCCM uses a concept with location roles that handle specific functions in SCCM management [7]. You need to add the Windows Intune Connector in the SCCM management console to the Administration | Overview | Site Configuration | Servers and Site System Roles node.
There is no need to modify the Intune Connector configuration. During the connector install, an additional Site System Role (Site System Server) named manage.microsoft.com is added; this is not configurable. Proceed by checking that the Site System role has installed correctly by checking the Monitoring | Overview | System Status | Site Status node in the SCCM management console [8].
Managing Mobile Devices
After installing the Intune Connector, you now have the matching extensions in the SCCM management console. They include support for Windows Phone 8.1, Apple iOS security setting, and email profile extensions to configure Exchange ActiveSync accounts on managed Apple iOS devices and support remote reset. To enable the extensions for Windows Intune, you need to terminate the SCCM management console and then launch it again.
Nothing should stop you from enrolling a mobile client now. Depending on the endpoint's platform and version, enrolling the device involves different activities. For example, you can download, register, and install the Intune enterprise portal application on Google Play for an Android device with version 4.0 or newer.
After installing the app, the device owner needs to log in with their Intune account and confirm the message on management through enterprise device policies. Then, the enrollment process in Intune starts, and the enrolled endpoint should immediately appear in the Intune management console and in the SCCM management console after a brief delay.
SCCM uses the Windows Intune Subscription to communicate with cloud services. SCCM administrators can now draw on many of the well-known SCCM technologies and management tasks to manage mobile devices, access hardware and software inventory features, or distribute apps to the endpoints. Additionally, policies for mobile devices can be created in the Intune management console and assigned to devices and device groups. The configuration options in the Intune policies go well beyond those for creating mobile device policies in Exchange Server 2013 and are easily on a par with many other commercial mobile device management offerings.
« Previous 1 2 3 Next »
Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.







