« Previous 1 2 3 Next »
Kubernetes Auto Analyzer
Securing Kubernetes
Pipe Down
A couple of approaches can be taken to install Kubernetes Auto Analyzer: a Docker container or a Ruby Gem.
I will take the potentially trickier Ruby route to show you how I got it working. The tool needs a working Ruby environment to run correctly. Fret not, because I will run through the packages required on a freshly released (at the time of writing) stock CentOS 7.5 build first, which should also work for the better part on modern Fedora and Red Hat Enterprise Linux builds, too. If you already have a few of these packages installed, then simply add the ones not present.
If you are interested in using a Debian derivative, I have also successfully run Kubernetes Auto Analyzer on Ubuntu 16.04 without headaches. I’ll also briefly run through how I got it working on my Xenial 16.04 build, which admittedly might already have had a few of the required packages installed.
Occasional, irritatingly subtle package name changes occur between Linux flavors and distributions, but a quick Google search should reveal the package name you need to get your installation working. Don’t let your package manager’s ignorance of a certain package confuse you, just persevere. Dare I also say at this point, if you haven't guessed already, that you need a working Kubernetes installation?
For clarity’s sake, I would begin by running the sophisticated auditing tool on the Kubernetes Master node, first. When you run it on a slave (aka worker and, previously, minion) node, you will be able to check against any plaintext authentication security holes when the slaves communicate with the API server, which assists in running the Kubernetes cluster. From what I’ve seen, this usually applies to the defaults in older Kubernetes versions.
To demonstrate the tool’s potential, I’m going to use a local Minikube installation on my laptop to generate a report. (Minikube is a sophisticated, localized, stripped-down Kubernetes build that is great for testing and lacks the complexities a cloud cluster brings.)
A Wide Berth
I’ll start with a look at the CentOS 7.5 Kubernetes Auto Analyzer build packages. I’ve noticed that some cloud providers alter their stock Linux distributions a little to suit their own cloud environments. For example AWS might point the default NTP (Network Time Protocol) servers on a Linux machine image to an internal AWS time server, which lessens the need to talk to the Internet and reduces the server’s attack surface. Incidentally, AWS and, I think, Ubuntu 18.04 LTS are now mostly using Chrony; chronyd is a stripped-down NTP server for extra security. As a result, the mileage involved in the installation of the required packages may vary.
The packages installed in Listing 1 give you a good pointer toward a sane and working Ruby environment for your Kubernetes security testing. As you can see from the list of commands, I created a bare-minimum Ruby build on CentOS 7.5 working with Ruby gems. Figure 1 shows the final command needed to install the gems that get the security tool functioning.
Listing1: Installation on CentOS 7.5
$ yum update $ yum -y upgrade; reboot $ yum install ruby-devel.x86_64 $ yum install -y libxml2-devel libxslt-devel $ yum install -y autoconf automake libtool bison $ yum install -y gcc-c++ patch readline readline-devel zlib zlib-devel $ yum install -y libyaml-devel libffi-devel openssl-devel make bzip2 $ gem install public_suffix -v 2.0.5 $ yum info ruby # Needs to be v2.2+ $ curl -sSL https://rvm.io/mpapis.asc | gpg --import - # From here see https://tecadmin.net/install-ruby-latest-stable-centos $ curl -L get.rvm.io | bash -s stable $ source /etc/profile.d/rvm.sh $ rvm reload $ rvm requirements run $ rvm install 2.5 # This may take a while $ rvm list $ rvm use 2.5 --default $ ruby --version $ gem update # Errors not related to kubeclient or kube_auto_analyzer don't stop it working $ gem install --no-document json kubeclient kube_auto_analyzer
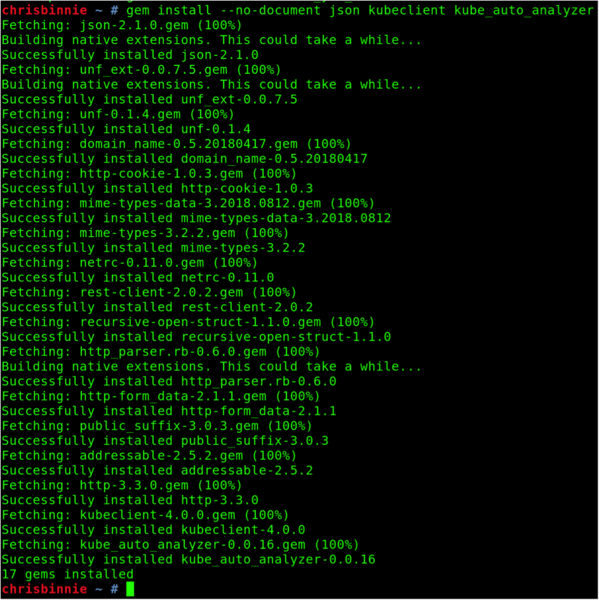 Figure 1: Success is denoted by Ruby’s gem being happy at the end of the process, as seen with the CentOS 7.5 Linux distribution.
Figure 1: Success is denoted by Ruby’s gem being happy at the end of the process, as seen with the CentOS 7.5 Linux distribution.
In case you’re wondering, I needed to bump up the Ruby version (I chose v2.5), and I used rvm , which was perfectly documented online. If you get a bit lost with my notes and the rvm section, then just refer to the documentation. I’ve tested these commands on a cloud platform I’ve recently discovered called Vultr. They’re worth a look if you’re not aware of their service. I’ve been suitably impressed in terms of cost and quality so far.
Keeling Over
For the Ubuntu 16.04 build, I used the following packages:
$ apt install rubygems-integration $ apt install ruby-all-dev $ apt install gem $ apt install -y make bzip2 $ gem install --no-document json kubeclient kube_auto_analyzer
Remember, I might already have had some of the packages shown in the CentOS commands in Listing 1 installed, because my Ubuntu laptop is well used. If these commands don’t work for you, you can look up the equivalent Ubuntu packages or go down the Docker route. The installation commands here show the packages I needed.
« Previous 1 2 3 Next »
Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.







