
Lead Image © Natalia Lukiyanova, 123RF.com
Preparing for cyberattacks
The Enemy in My Web
The number of cyberattacks with ransomware has been rising steadily for several years. WannaCry ransomware attacks caused quite a stir in 2017. Hundreds of thousands of Windows systems were infected through a vulnerability in Microsoft's SMB protocol, and the data on these systems were encrypted. The malware used a US National Security Agency (NSA) exploit named EternalBlue published for propagation by a hacker group. Although Microsoft released a patch to close this gap before the WannaCry outbreak, many systems had not yet been updated and were therefore still vulnerable (Figure 1).
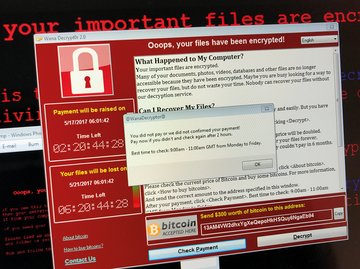 Figure 1: Game over. If you see a message like this on the screen, ransomware – in this case WannaCry – has struck.
Figure 1: Game over. If you see a message like this on the screen, ransomware – in this case WannaCry – has struck.
More or less by accident, British security researcher Marcus Hutchins found a way to disable WannaCry. The malware checks for the existence of a special domain before encrypting files. If the domain is not accessible, WannaCry starts encrypting. After the registration of this domain in the worldwide DNS system, further propagation was temporarily stopped after just four days. By then, Bitcoin payments equivalent to several hundred thousand dollars had already been transferred to the attackers' wallet.
The encryption of more than 30 servers on the computer network of University Hospital Düsseldorf in the fall of 2020 by a modified WannaCry variant attracted a great deal of attention in the German media. Because IT was unavailable at the hospital, one patient likely died because she could not be admitted and had to be transported to a hospital further away.
Access Vectors
In most cases, the goal of ransomware is to extort a ransom. Emotet [1] and EternalBlue [2] are just two of many ways criminals take control of computers and encrypt existing files. The Emotet botnet was dismantled by Europol investigators in early 2021 and the infrastructure was shut down. However, this huge success on the part of the European authorities only alleviated the threat situation for a short while. The first modified Emotet variants were already in circulation by November 2021.
In addition to email and security vulnerabilities, leaked employee login credentials offer a regular gateway into corporate networks, as illustrated by the Colonial Pipeline case in the US [3]. Attackers apparently found valid account credentials for an employee on the Darknet, accessed the company's computer systems over a virtual private network (VPN), and installed ransomware. As a result of the encrypted files and the ransomware, Colonial shut down the entire pipeline system for more than five days. The resulting shortfall in fuel supply led to a sharp rise in fuel prices in some parts of the US.
Colonial paid the equivalent of nearly $5 million in ransom to the extortionists. However, the extortionists did not simply rely on encrypting Colonial's files. Instead, they copied almost 100GB of files from the Colonial systems beforehand. The blackmailers additionally threatened to publish this information if Colonial did not pay the ransom. This practice of copying files before encrypting them opens another attack vector. Affected companies will still pay even if the data can be easily restored from a backup to prevent the publication of internal data and possible company secrets.
Perpetrator and Victim
The perpetrators of large ransomware incidents are mostly well-organized groups. After postmortem investigations and publications, the hacks are repeatedly attributed to hacker groups in Eastern Europe or Russia. This attribution primarily relies on analyzing the malware and the perpetrators' communication with their victims, but small groups of perpetrators also use ransomware, although they do not develop it themselves. Ransomware construction kits can be found on various forums for a small sum.
If you look at the public coverage of ransomware incidents, you can't help feeling that it is mainly large institutions and public bodies that are targeted. However, this image is deceptive. Small and medium-sized enterprises (SMEs) are just as much victims of ransomware as are private individuals. SMEs in particular sometimes suffer massive damage after cyberattacks. No official figures indicate in how many cases the ransom was paid; however, the continued high number of attacks is an indication that the method is successful.
Although the perpetrators are often not choosy in their victims, they do take a targeted approach after a successful raid by analyzing the network infrastructure so they can hijack as many systems as possible. Moreover, backup systems are identified to make the recovery process more complicated. Only after the attackers have grabbed the sensitive data does the encryption process begin, with the ransom demand following on its heels.
Although private computers might not seem particularly worthwhile targets at first glance, the consequences can be explosive – even if the owner does not pay a ransom – because the attackers also collect passwords from the usual password safes of the browser or email program. Although these passwords are often secured by a master password, the master can be sniffed. In many cases, access credentials for other computer systems are also preserved in these records, which is how criminals repeatedly find login data for remote maintenance access. The perpetrators then use the data to access corporate networks, which in turn means they have found another victim for their malware.
Protections
Different measures are required to protect yourself successfully against ransomware and the possible consequences of an infection (see the "Cyber Insurance" box). Technical vulnerabilities, such as WannaCry and EternalBlue, can be removed by regularly updating all systems in the company. With regard to automated updates, you first need to ask yourself for each system whether a potential failure because of an error during the update process outweighs an existing security vulnerability. You will want to enable automatic updates where possible, even at the risk of failure because of a failed update. The longer it takes to review and release an update, the more time attackers have to access enterprise systems.
Cyber Insurance
If you want to protect yourself against the consequences of cyberattacks, you can resort to the classic means of insurance and take out cyber insurance. Depending on the industries in which you operate, cyber insurance can be a beneficial addition to your risk and contingency plan. Insurance companies can also help you take initial steps after an attack has occurred and refer proven incident analysis partners. Whether or to what extent the consequences of the attack are covered and whether the insurance company will pay a ransom depends on your individual contract. However, some major insurance companies announced last year that they would no longer pay ransom to criminals.
You will want to use centralized antivirus and application layer gateways to scan email attachments before they are delivered to employee accounts. At least the malware variants created by construction kits can often be detected in this way, although they often do not work against the individual variants of the larger groups.
To prevent retroactive loading of malware after an infection, you can redirect your employees by web proxies, prohibit binary downloads or enable them separately, and initially block all other requests to pass by the proxy in the packet filter. Security product providers offer lists of IP addresses and domains that you need to filter for this purpose. These measures often cannot be implemented without restricting employees, and they sometimes interfere with daily work. Therefore, many companies do without them. However, it makes sense to work with other staff to see which measures you can implement. You can also take into account the times when no one usually works. When your office is closed, you can implement and monitor far stricter rules, which are then relaxed again during normal business hours.
Even though a company's users are always portrayed as the highest risk vulnerability, they are really your last line of defense and can prevent an infection, unlike the industrial security products such as antivirus programs, application layer gateways, and special firewalls.
Attackers use spearphishing techniques and, as in the case of Emotet, existing communications to trick users into running the malware. Seeing through these perfidious techniques is difficult even for well-educated and trained employees. Educating your users needs to be an integral part of your overall IT security strategy. Targeted training (including an active error culture and an option to report conspicuous activities) sensitizes your users so that they do not involuntarily help the attackers.
Additionally, you can provide technical support to your employees and establish email signing in your organization to make it at least a little more difficult to create credible email. If all the email in your organization is signed, those messages that aren't will stand out. The fewer exceptions, the more reliably your employees can detect fake email. However, if a user opens a malicious attachment, you need to protect the system with active group policies that prohibit the execution of macros in these files. If users need macros for their daily work, then at least use signed macros and prevent unsigned macros from running.
Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.





