Lead Image © Maksim Kabakou, 123RF.com
SSH tools for Windows
Safe Connection
This article presents advanced Secure Shell (SSH) functionality and SSH-based tools for use on Windows. It does not question the fact that both Linux (vsftpd, proftpd) and Windows (IIS) let you operate a secure FTP server with standard tools and that there are countless secure and powerful FTP clients. The charm of SSH consists above all in being able to use remote logins, file transfers, port forwarding, VPN, and other functions ad hoc without extensive preparatory measures. For SSH, you only need to run the SSH daemon, sshd, on the (Linux) server.
SSH offers maximum security thanks to these three properties:
- Encryption of transferred data, including login information.
- Protection against manipulation of the transferred data (data integrity).
- Authentication of the communication partner.
SSH always uses transmission encryption; it can use the default host key to ensure the integrity of the connection or the hosts, and it supports peer authentication. Although SSH "only" works by default with usernames and passwords, it also optionally supports asymmetric DSA and RSA key pairs.
SSH Basics
The free Linux SSH Version, OpenSSH, is a spin-off of the classic SSH from 1999. The popular Windows SSH client PuTTY, developed by Simon Tatham, is also a free SSH implementation. It is subject to the MIT license and is currently at version 0.62 from 2011. All versions of SSH are largely compatible.
The term Secure Shell is the umbrella for a bunch of remote access tools. The entire SSH suite contains the following tools:
ssh– Replacesrsh,rlogin, andtelnet.scp– Replacesrcp.sftp– Replacesftp.sshd– The SSH server daemon.ssh-keygen– Generates asymmetric public keys for authentication or manages or converts keys.ssh keyscan– Searches for existing SSH public keys.ssh-agent– Keeps the private key in memory until the user logs out.ssh-add– Loads a private key intossh-agent.
The PuTTY Suite [1] offers the same variety of tools. To begin, admins must download the complete zip archive with all the PuTTY SSH tools and not just run the .exe installer, which only downloads and installs the PuTTY SSH client. However, the respective tools have slightly different names in PuTTY, such as puttygen or psftp. In addition to the popular PuTTY, Windows admins have options for using SSH on Windows, such as the Cygwin Windows X server-based MobaXterm [2] [3] or direct use of the Cygwin API compatibility layer [4].
Enabling SSH
Setting up the SSH server on the Linux side – the SSH client generally is installed by default – is not the subject of this article, but you can do this by installing the openssh-server (RHEL, Fedora) or openssh packages (the SUSE package contains the server and client) with the preferred package management tool.
To enable the service, you need to start the sshd daemon and possibly add it permanently to the system boot configuration. You can do this, depending on your choice of distribution, with /etc/init.d/sshd start (SysV), service sshd start (Upstart), or systemctl start sshd.service.
Additionally, the service – if so desired – must be permanently added to the system boot configuration. For this step, you could use systemd (openSUSE, Fedora) by typing systemctl enable sshd.service or chkconfig sshd on (RHEL/SysVinit). On Fedora and Red Hat, you need to stop the firewall, which runs by default, by typing systemctl stop iptables.service, or create a rule for port 22 (SSH).
Administrators typically do not need to make any adjustments to the main configuration file – usually /etc/ssh/sshd_config – with one exception. The exception is that many OpenSSH implementations prevent root access by default; uncommenting the following line:
PermitRootLogin yes
lets you enable it.
Dealing with Host Keys
For Linux admins, dealing with the SSH host key is part of everyday life. Because a successful SSH connection requires a user account on the remote host, all SSH tools perform an authentication process. On Linux, typing
ssh -l <username> <remote IP address>
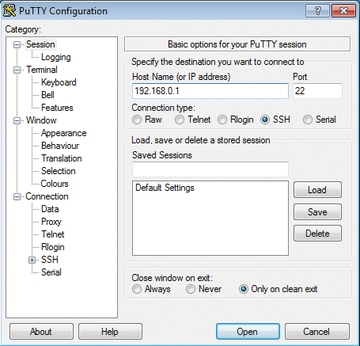
is sufficient to open a connection to the remote server, which then asks for the password to match the specified username and transfers the usernames and passwords in encrypted format. The process is the same for PuTTY, but you might not immediately notice, because the login takes place behind the graphical interface (Figure 1). For PuTTY, you only need to enter the desired target host in the Host Name field of the default Session tab.
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.