Lead Image © Suzanne Tucker, 123RF.com
Monitoring IPv6 with Wireshark
New Dust with Old Brooms
Sys admins around the world use the free network protocol analyzer Wireshark to monitor traffic and troubleshoot problems on TCP/IP networks. If you're wondering whether you'll still be able to use Wireshark in the IPv6 era, the answer is yes, but you'll need to be aware of some important differences between the IPv4 and IPv6 protocols. This article begins with some background on IPv6 and shows you how to get started with using Wireshark to monitor IPv6 communications.
About IPv6
Like an IPv4 address, an IPv6 address consists of two parts: The left side represents the network identifier, and the right side represents the host ID. The default prefix is /64 and divides the IP address into two halves, the routing area and the interface address (64 bits each). An IPv6 address consists of 128 bits and is usually expressed as eights sets of four hexadecimal digits (known as nibbles, quibbles, or hextets) separated by colons. For example, an IPv6 address looks like this: 2001: 0db8: 1010: 61ab: f005: ba11: 00da: 11a5 / 64 .
In Europe, providers obtain IPv6 addresses through the Réseaux IP Européens Network Coordination Centre (RIPE-NCC) and then pass them on to users. A user who receives an IPv6 address is not actually the owner of the address. Instead, the user enters into a user agreement. All allocations are subject to the allocation guidelines.
IPv6 Address Types
IPv6 distinguishes between unicast, multicast, and anycast addresses. A unicast address represents a single host; each interface of the host can have more than one unicast address. Hosts are usually assigned two types of IPv6 unicast addresses: link local and global unicast addresses.
A link local address is similar to the private address in the IPv4 world and is used for communication on the local network (for example, with other hosts or routers connected to the network). These addresses are not routable and each network interface has only one link local address. You can recognize these addresses by the network identifier FE80:: /10 (but the host identifier actually starts after the 64 bits). Once IPv6 is enabled on a network interface, it generates a link local address. The link local address can be defined in any of the following ways:
- Manual: The address is configured manually on the host.
- Modified IEEE EUI-64 format (according to RFC 4291): The host ID is derived from the MAC address of the network interface.
- Privacy Format (according to RFC 4941): The host ID is based on a random number.
After a network interface receives a link local address, it sends a multicast message to all hosts on the local network. Using Duplicate Address Detection (DAD), the interface ensures that no other host with the same address is active on the local network.
Communication via Neighbor Discovery Protocol
The Neighbor Discovery Protocol (NDP) is an additional protocol defined in RFC 4861 and is the equivalent of the Address Resolution Protocol (ARP) of IPv4. NDP enables the IPv6 interface to detect and communicate with neighboring computers and routers. NDP defines the following Internet Control Message Protocol (ICMP) messages:
- Neighbor Solicitation (NS): A host sends these messages via multicast when searching for a link local address or when confirming that the generated link local address has not been assigned to another host (DAD). NS messages show the ICMP value
135. - Neighbor Advertisement (NA): A host reacts to a NS message. This message is similar to the ARP response in IPv4. NA messages have an ICMP value of
136. - Router Solicitation (RS): A host sends this message via multicast to automatically detect the routers available in the local network. RS messages have the ICMP value
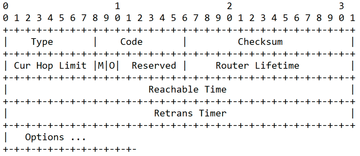
133. - Router Advertisement (RA): With the help of RA messages, a router identifies itself to all hosts in the network and simultaneously transmits the necessary network information to all hosts (Figure 1). RA messages have an ICMP value of
134.
For more on ICMP values, see the box entitled "ICMP in IPv6."
ICMP in IPv6
ICMP is a supporting protocol used for sending error and information messages. The version of ICMP used with IPv6 (called ICMPv6) includes a code field used to transmit specific information about the state of communication. Values between 0 and 127 are error messages. Values between 128 and 255 are informational messages.
RA lets routers announce their presence on the network. Messages are sent either on request via RS or periodically (to avoid being forgotten). The hop limit is an 8-bit value that transmits the standard hop limits suggested by the router. The flags contained in the RA messages define the automatic address configuration method:
- A set M bit tells the node to use stateful autoconfiguration in addition to autoconfiguration for the IP address.
- A set O bit tells the node that it can use stateful autoconfiguration in addition to autoconfiguration for all non-IP address information.
- A set HA bit indicates whether a home agent is active for mobile accessibility.
- The Pref bit can be used to set the preferences for several routers on the network.
- Proxy bits indicate whether a proxy is being used.
The router lifetime is a 16-bit integer value that specifies how many seconds a router should remain in the default router list. The theoretical maximum is just over 18 hours (65,536 seconds), but RFC 4861 limits the maximum to 9,000 seconds (2.5 hours). A value of 0 means that the router is not a default router and should not be entered in the default router list.
The router lifetime is a 32-bit integer value that specifies how many milliseconds an entry in the Neighbor cache should still be considered reachable after receiving data. And the Reachable Time specifies the number of milliseconds after which a new NS message should be sent.
Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.