« Previous 1 2 3 4 Next »
Endpoint Security for Windows 10
Well-Tempered Computer
Defender Credential Guard
Defender Credential Guard [6] is one of the most important newer features in Windows 10. It also uses Hyper-V virtualization-based security features to isolate secrets such as passwords, password hashes, and Kerberos ticket-granting tickets and gives access only to privileged system processes. NTLM (new technologies LAN manager) hashes or the well-known pass-the-hash or pass-the-ticket attacks are no longer possible in this case (Figure 2). Defender Credential Guard requires the use of Windows 10 Enterprise or Windows Server 2016 and has the following hardware requirements:
- Virtualization-based security (VBS): VBS requires a 64-bit CPU, enabled CPU virtualization extensions, extended page tables, and a Windows hypervisor.
- Secure boot
- Trusted Platform Module (TPM) 2.0 (recommended)
- Unified Extensible Firmware Interface (UEFI) lock (recommended)
Defender Credential Guard is configured by group policies.
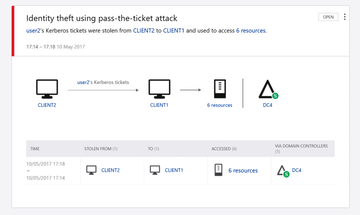 Figure 2: The Advanced Threat Analytics console quickly identifies security incidents in the directory service.
Figure 2: The Advanced Threat Analytics console quickly identifies security incidents in the directory service.
Defender Exploit Guard
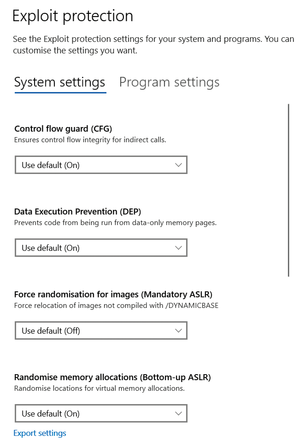
Defender Exploit Guard (WDEG) [7] is provided by Microsoft starting with Windows version 1709. WDEG provides a set of host intrusion prevention features to reduce the attack surface on user applications. It is the successor to the Enhanced Mitigation Experience Toolkit (EMET), which Microsoft also makes available for free download for older versions of Windows to protect against exploits in applications that use techniques such as data execution prevention, address space layout randomization, structured exception handling overwrite protection, and others. WDEG can be configured in the Defender Security Center (Figure 3).
Defender Exploit Guard extends the security features provided with EMET to include Control Flow Guard, which provides protection against memory corruption by restricting where applications can execute program code and extends existing exploit prevention technologies.
Defender SmartScreen
SmartScreen has been part of the operating system on clients and servers for several Windows versions and was renamed Microsoft Defender SmartScreen [8] in Windows 10. The tool helps prevent access to websites that have been reported as phishing or malware spreaders and blocks the download of potentially dangerous files. Defender SmartScreen determines whether a web page is potentially dangerous as follows:
- Analyzes web pages visited and searches for indications of suspicious behavior. If this is the case, SmartScreen displays a warning page and advises caution.
- Compares web pages visited with a dynamic list of reported phishing and malware portals. In case of a match, SmartScreen also displays a warning that the website may be malicious.
SmartScreen tries to determine whether a downloaded app or app installer might be dangerous in the following ways:
- Compares downloaded files with a list of reported websites and programs with malware known to be unsafe. In case of a match, SmartScreen displays a warning to that effect.
- Compares downloaded files with a list of known files downloaded by many Windows users. If the file does not appear in this list, SmartScreen displays a warning and advises caution.
SmartScreen is configured by Active Directory group policies or a mobile device management tool such as Microsoft Intune.
« Previous 1 2 3 4 Next »
Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.