Figure 1
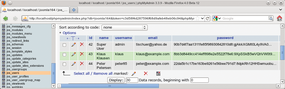
Figure 1: If an attacker has access to the database, they will only see cryptic hash. In this example, PhpMyAdmin shows the Joomla Content Management System, which uses the MD5 approach with a salt.