Figure 6
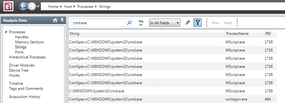
Figure 6: Using the Redline Strings output to look for additional evidence of malware.

Figure 6: Using the Redline Strings output to look for additional evidence of malware.