Figure 4
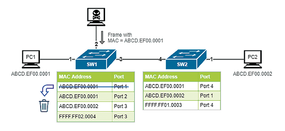
Figure 4: The MAC address table is overwritten by the fake record so that all traffic with destination address ABCD.EF00.0001 will go to the attacker's port.

Figure 4: The MAC address table is overwritten by the fake record so that all traffic with destination address ABCD.EF00.0001 will go to the attacker's port.