Figure 5
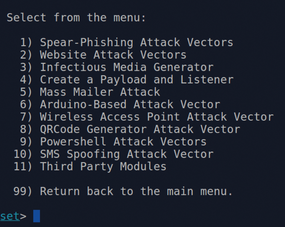
Figure 5: A list of social engineering attacks.

Figure 5: A list of social engineering attacks.