Figure 5
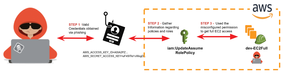
Figure 5: Phishing for valid AWS credentials.

Figure 5: Phishing for valid AWS credentials.