Figure 2
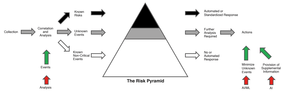
Figure 2: The challenge in IT security is to minimize and target unclear events.

Figure 2: The challenge in IT security is to minimize and target unclear events.