Figure 6
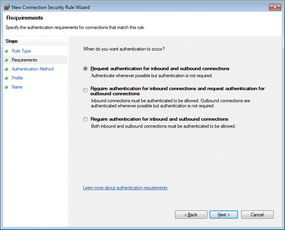
Figure 6: Specifying authentication requirements for rules.

Figure 6: Specifying authentication requirements for rules.