Figure 4
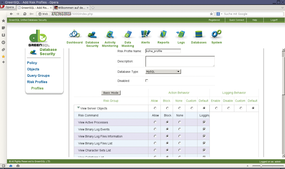
Figure 4: Risk profiles give administrators a granular approach to defining which database operations are allowed and which are not.

Figure 4: Risk profiles give administrators a granular approach to defining which database operations are allowed and which are not.