BackTrack Linux: The Ultimate Hacker's Arsenal
Penetration Testing and security auditing are now part of every system administrator's "other duties as assigned." BackTrack Linux is a custom distribution designed for security testing for all skill levels from novice to expert.
Penetration (Pen) testing and security auditing are now part of every system administrator's "other duties as assigned." BackTrack Linux (http://www.backtrack-linux.org/) is a custom distribution designed for security testing for all skill levels from novice to expert. It is the largest collection of wireless hacking, server exploiting, web application assessing, social-engineering tools available in a single Linux distribution.
BackTrack Linux is a fine example of a specialized Linux distribution. Its only purpose is to test your network, devices, and systems for security vulnerabilities. BackTrack is packed with every security and hacker tool used by security professionals and professional hackers. If you're looking for all of the tools in one place, this is it.
You must love the command line to use this distro, although it does contain a few graphical tools, such as zenmap and wireshark. Even in graphical mode (which comes up with the Gnome desktop), most of the applications open in a terminal window. Fortunately, each command line application opens and displays the help text so you can refer to the command reference right there on the screen.
BackTrack is a highly customized, Debian-based Linux distribution that you should only update through BackTrack's own repositories (http://all.repository.backtrack-linux.org/).
What Do You Get For Nothing?
BackTrack Linux contains more than 300 security tools and utilities that are all open source. Many security professionals prefer them over expensive commercial programs. And, hackers certainly prefer hundreds of no cost, high-end applications to anything commercial. One reason for BackTrack's popularity is its anonymity. You don't have to register (Registration is optional). No names, bank accounts, or user accounts are associated with obtaining the ISO image. Additionally, no spyware will report back to any vendor.
In short, BackTrack's tagline says it all: "The quieter you become, the more you are able to hear."
The distro is a bootable, live DVD that's approximately 2GB in size. If you decide to install it to a hard disk or USB drive, the installation expands to almost 7GB. BackTrack is perfectly suited to installation to a USB drive, so that it's portable and stealthier than a hard disk install. A 16GB USB drive holds the installation with plenty of room for saving files and data.
Remember that you'll need to save your data from your information gathering exercises so that you can write security audit reports for your clients. The Live DVD is powerful but considerably slower than a hard disk or USB disk. If you use the DVD, use a USB drive or mountable hard disk partition to save the information you gather.
What's Included in the Distro
The BackTrack Distribution includes the following major tool categories:
- Information Gathering
- Vulnerability Assessment
- Exploitation Tools
- Privilege Escalation
- Maintaining Access
- Reverse Engineering
- RFID Tools
- Stress Testing
- Forensics
- Reporting Tools
- Services
- Miscellaneous
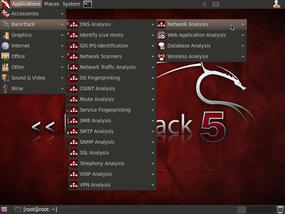
Under each of the main headings, you'll find subheadings. For example, under the first selection, Information Gathering, you have Network Analysis, Web Application Analysis, Database Analysis, and Wireless Analysis. Under each of those subheadings, you have multiple types of analyses. The Network Analysis subheading contains an extensive list of network analysis types from DNS Analysis to VPN Analysis, as shown in Figure 1.
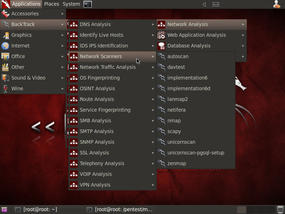
At the final level, you'll find multiple choices for each type of analysis. For example, under Network Scanners, you have a list of 11 different network scanning tools from which to choose. See Figure 2.
Flying Under the Radar
Your main goal in any penetration testing episode is to tread lightly so that you don't set off any intrusion detection alerts or cause a noticeable amount of activity on the systems and network in which you're working. Your activity must not look unusual to network engineers or other system administrators. Why? Because you're often working in stealth mode when checking system security. If you're an external consultant who's hired to check and report on security, you want to work as silently as any hacker would who wants into that network. Few, if any, ever come in with guns a-blazing.
One easy way to gather a lot of information on your target network quickly is to perform a SYN scan with Nmap. Nmap may well be the hacker's most powerful piece of software. (An example of Nmap is included in the Examples section at the end of this article.) A SYN scan doesn't make complete connections to a system's services.
A SYN scan never completes the TCP handshake process and therefore the target host never logs the attempt, so no alarms are triggered. (This technique works because TCP/IP is a "polite" protocol. It doesn't speak until spoken to.)
The port scanner sends out a SYN request on a particular port number (22). The target responds with an ACK. The scanner notes the ACK and sends a RST to disconnect from the target. No TCP connection ever takes place. The port scanner sends a SYN request to the next likely open port number, and so on.
A non-computer example might help explain this concept better. You walk up to a house on your street and ring the doorbell (your SYN request), the homeowner walks to the door to offer a greeting (The ACK "Acknowledgement") but you've run away before the homeowner could open the door, still watching close by to see that the door opened and making sure someone is indeed home. The homeowner closes the door and goes back inside the house and waits for the next doorbell ring (The RST "Reset"). The homeowner doesn't call the police because there's no damage nor any intruder to be found (No system logs or alerts).
The SYN scan is very clean (leaves no trace) because no harm is done to the target. This type of scan works on all operating systems.
It's important to remain as quiet as possible during your reconnaissance phase so you can gather as much information as possible about systems and their potential vulnerabilities without detection. Remember too, that it's not always necessary to use another method to collect operating system type. You can identify some operating systems by the identification of their open ports.
Hacking Your Neighbor's WiFi Connection
With great power comes great responsibility. BackTrack Linux is a tool. It has no conscience nor does it have any evil purpose. Its developers provide it to you at no cost for the purpose of legitimate penetration testing. You could use BackTrack to illegally hack into lots of things: websites, systems, and even your neighbor's WiFi connection. You could also spend some years in jail for doing those things. BackTrack Linux is for penetration testing on systems that you have responsibility for or on systems for which you've been hired to test. It is not for illegal hacking or system compromise.
Companies, including the one you work for, your ISP, and your neighborhood coffee shop, have different levels of tolerance for port scanning, attempted cracks, and unauthorized system security checking. If you do not have permission to perform penetration testing against systems, sites, and network components, don't do it.
Always ask for permission before performing any of these tests on systems you don't own. And, make sure you obtain that permission from someone who has the authority to give it.
Examples
Although the BackTrack site offers a long list of tutorials, and you can sign up for hacking classes online with their affiliated Offensive Security site (http://www.offensive-security.com/), the following two examples are good starting places for new security professionals. If you're a system administrator wanting to check a few basic security points on your systems, these two will do it for you.
Zenmap/Nmap
You'll find Zenmap under BackTrack | Information Gathering | Network Analysis | Network Scanners. Select zenmap from the list. Refer to Figure 2 from the previous section. Zenmap is the graphical interface for Nmap. If you aren't familiar with Nmap's extensive command list, Zenmap makes Nmap easier by allowing you to make selections via the graphical interface. Nmap is an extremely powerful and complex tool. Its man page is very long and involved. See http://linux.die.net/man/1/nmap for an online version. As an aid to your learning, Zenmap shows the equivalent Nmap command for each sweep you perform.
If you perform the simplest scan of a host (target), Zenmap provides a huge amount of information very quickly. To perform a quick scan of a target, enter its DNS name or IP address into the Target field, select a scan type (Default: Intense scan) from the dropdown list, and click the Scan button.
The Nmap command line equivalent of this scan is:
nmap -T4 -A -v 192.168.1.250
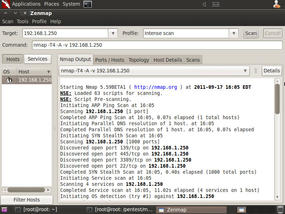
See Figure 3 for a screen shot of Zenmap in action.
You can see from the first part of the scan that Nmap begins with an ARP Ping scan, then a DNS resolution check, then a port sweep to detect and identify open or listening ports, and then it attempts to detect the target's operating system.
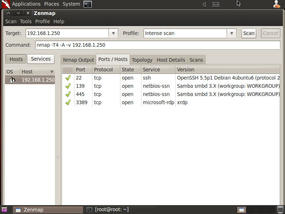
Select a tab to view more detailed information on the scan's results. See Figure 4 for port scan information from the Ports/Hosts tab.
You'll often see exact version information related to listening services on a host, which helps you determine vulnerabilities and exploitable services.
Nmap is an advanced tool that is widely used among security professionals and hackers. It provides a great deal of information for the least amount of effort. For an exhaustive look at Nmap and Zenmap, I recommend Nmap In The Enterprise: Your Guide to Network Scanning, Syngress Publishing, 2008, Orebaugh and Pinkard. You'll also find a reference guide and other documentation at the Nmap website (http://nmap.org/).
Ncrack
Ncrack is a highly effective and fast network authentication cracking tool. Its purpose is to assist you in identifying user accounts with weak passwords without the hassle of logging into each host and cracking a password hash. Using it, you can check for weak FTP, SSH, TELNET, HTTP(S), POP3(S), SMB, RDP, and VNC passwords.
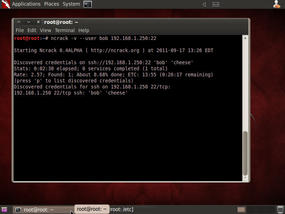
Figure 5 shows what an actual ncrack scan looks like after a successful password crack. The user account, bob, uses a very weak password: cheese. It took ncrack two minutes thirty seconds to crack this password. This means that a hacker could login to this system using the 'bob' account in less than five minutes and commence working on breaking a privileged account or downloading malware with ease.
System security is serious business, and you should understand the tools that hackers use to compromise your systems. By running your own checks first and strengthening your defenses, you could save your company millions of dollars in losses. Security is everyone's business, and it is your job.