« Previous 1 2
Understanding Cybersecurity Maturity Model Certification
Ready, Steady, …
CMMC 2.0
In March 2021, the DoD initiated an internal review of CMMC's implementation, informed by more than 850 public comments in response to the interim DFARS rule. This comprehensive, programmatic assessment engaged cybersecurity and acquisition leaders within DoD to refine policy and program implementation, and in November 2021, the DoD announced CMMC 2.0 [5]. The view is that version 2.0 would achieve the primary goals that came out of this internal review:
- Safeguard sensitive information to enable and protect the warfighter.
- Dynamically enhance DIB cybersecurity to meet evolving threats.
- Ensure accountability while minimizing barriers to compliance with DoD requirements.
- Contribute toward instilling a collaborative culture of cybersecurity and cyber resilience.
- Maintain public trust through high professional and ethical standards.
The enhanced CMMC 2.0 program maintains the program's original goal of safeguarding sensitive information while trying to simplify the CMMC standard and providing additional clarity on cybersecurity regulatory, policy, and contracting requirements. The US government believes this is achieved by focusing the most advanced cybersecurity standards and third-party assessment requirements on companies supporting the highest priority programs and increasing Department oversight of professional and ethical standards in the assessment ecosystem.
The program is meant to ensure accountability for companies to implement cybersecurity standards while minimizing barriers to compliance with DoD requirements, as well as instill a collaborative culture of cybersecurity and cyber resilience and enhance public trust in the CMMC ecosystem, while increasing overall ease of execution. Jesse Salazar, Deputy Assistant Secretary of Defense for Industrial Policy, one of the leaders of the CMMC effort, said [6]:
CMMC 2.0 will dramatically strengthen the cybersecurity of the defense industrial base. By establishing a more collaborative relationship with industry, these updates will support businesses in adopting the practices they need to thwart cyber threats while minimizing barriers to compliance with DoD requirements.
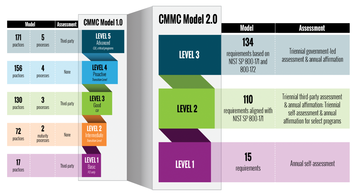
Figure 1 shows the difference between CMMC versions 1.0 and 2.0. With the implementation of CMMC 2.0, the Department is introducing several key changes that build on CMMC 1.0 and refine the original program requirements:
- A streamlined model that focuses on the most critical requirements and reduces the model from five to three compliance levels. This change aligns CMMC 2.0 with widely accepted standards and uses NIST cybersecurity standards.
- Reliable assessments reduce assessment costs and allow all companies at level 1 (Foundational) and a subset of companies at level 2 (Advanced) to demonstrate compliance through self-assessments. Higher accountability increases oversight of professional and ethical standards of third-party assessors.
- Flexible implementation encourages a spirit of collaboration that allows companies, under certain limited circumstances, to make plans of action and milestones (POA&Ms) to achieve certification. The added flexibility and speed allow waivers to CMMC requirements under certain limited circumstances.
CMMC Is Coming
Whether you like it or not, the DoD is planning to release an interim rule on the CMMC framework by May 2023, according to Stacy Bostjanick, director of the CMMC program for the DoD [7]. CMMC will be enacted on the day the interim rule is published, and CMMC requirements will start to appear in DoD contracts by July 2023, 60 days after publication of the interim rules.
Doing nothing is not an option. As of this writing, defense contractors have little more than a year to become CMMC compliant. If your company is still at the very beginning of this timeline, the time for action is now, although you might be able to take consolation on two fronts:
First, the time and effort needed to achieve compliance will be different for every defense contractor. Variables include your baseline cybersecurity maturity level and the resources and prioritization you can assign to achieving compliance. Your organization might need less time to achieve and demonstrate compliance, or you might be able to commit more resources and energy than a typical contractor would and so make up for lost time.
Second, under CMMC 2.0, it will be permissible to sign DoD contracts with a POA&M in place, which means your organization does not need to achieve the highest assessment score possible by May 2023. However, in case that lessens your sense of urgency, consider that CMMC 2.0 will bring critical changes to the reprieve that POA&Ms have historically offered. POA&Ms will most likely have time constraints. At this point, it seems that contractors will have 180 days to remediate security gaps identified in their POA&Ms, but that is subject to change during the CMMC 2.0 interim rule-making process.
Bostjanick also said recently [7] that the DoD is expected to permit POA&Ms only for the lowest-risk security controls (i.e., those that are worth just one point in the DoD's assessment scoring methodology). Fifty of the 110 security controls are worth one point. That leaves 60 controls that are worth either three or five points and must be met before a contractor's CMMC level 2 assessment. These 60 controls are both the most important for securing CUI and some of the most difficult to meet.
In short, although your organization doesn't have to achieve the highest possible assessment score by May 2023, it should be on the cusp of doing so by then. Your business risk is too high to be far behind the timeline of your organization's compliance journey.
Conclusion
A company's goal should not just be to achieve eligibility to win defense contracts, but also to minimize business risk and keep CUI out of the hands of adversaries. By getting started on your organization's compliance journey, you can achieve these objectives and ensure your company is ready for ramped-up federal enforcement of cybersecurity regulations.
Infos
- Defense federal acquisition regulation supplement: assessing contractor implementation of cybersecurity requirements (DFARS case 2019-D041). 85 Federal Register 61505 (Sep 2020), 18 p., https://www.federalregister.gov/documents/2020/09/29/2020-21123/defense-federal-acquisition-regulationsupplement-assessing-contractor-implementation-of
- Safeguarding covered defense information and cyber incident reporting (Dec 2019). DFARS 252.204-7012 (Sep 2022), https://www.acquisition.gov/dfars/252.204-7012-safeguarding-covered-defense-information-and-cyber-incident-reporting.
- "What Is the NIST SP 800-171 and Who Needs to Follow It?" by Traci Spencer. NIST , Oct 8, 2019, https://www.nist.gov/blogs/manufacturing-innovation-blog/what-nist-sp-800-171-and-who-needs-follow-it-0
- Basic safeguarding of covered contractor information systems. FAR 52.204-21 (Oct 2022), https://www.acquisition.gov/far/52.204-21
- "Strategic Direction for Cybersecurity Maturity Model Certification (CMMC) Program." US DoD release. Nov 4, 2021, https://www.defense.gov/News/Releases/Release/Article/2833006/strategic-direction-for-cybersecurity-maturity-model-certification-cmmc-program/
- "DOD launches CMMC 2.0 program; Jesse Salazar quoted" by Jane Edwards. GovConWire , Nov 5, 2021, https://www.govconwire.com/2021/11/dod-launches-cmmc-2-0-program/
- "Stacy Bostjanick shares updated DoD CMMC rollout schedule" by Summer Myatt. GovConWire , May 20, 2022, https://www.govconwire.com/2022/05/dods-cmmc-director-stacy-bostjanick-shares-updated-rollout-schedule/
« Previous 1 2
Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.