Lead Image © drubig-photo, fotolia.com
Automate the Active Directory Federation Services install
One Click
For this article on Active Directory Federation Services (ADFS) automation, I assume the work on Active Directory (AD) and DNS itself is complete and that the SQL Server is installed and available. The service account on the AD – in which context the service runs on each federation server – has no special permissions. However, it must be a member of the local Administrators group on each federation server. You can ensure this with a script or the following command at the prompt:
Net Localgroup administrators KBCORP\ADFSSrv /add
The NetBIOS name of the domain in the examples here is KBCORP , which you will see several times.
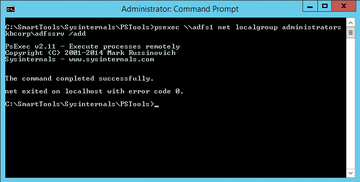
If you use multiple federated servers on your farm and want to populate the local administrator's group on the servers centrally and remotely, the Sysinternals PsExec.exe PSTools is a useful choice (Figure 1). In this age of PowerShell remoting and similar features, you have many ways to manage servers remotely, but few are as easy to handle as PSTools [1]. Without registering or installing anything on the target system or elsewhere, you can call PsExec.exe from any folder:
psexec \\adfs1 net localgroup administrators kbcorp\ADFSSrv /add...
Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.