« Previous 1 2 3 4 Next »
ASM tools and strategies for threat management
Choose Your Armor
Cloud Computing Aggravates Risk
Security experts consider cloud computing an important driver for the need for digital searches. Common practice in some companies is for specialist departments to subscribe to public cloud services on demand, often without informing the in-house IT department. Shadow IT of this kind exacerbates the situation for the IT team, because it becomes difficult to maintain an overview of the IT inventory and clutters access paths, pushing tried and trusted routines to their limits.
If the IT team has previously carried out vulnerability scans on a weekly basis, they could potentially miss a large part of this cloud dynamic. ASM, on the other hand, aims to scan the entire Internet to understand the elements of a company's infrastructure. For example, an ASM tool can map certificates of a cloud service to a company, even if the IT manager or chief information security officer (CISO) is not aware a department has booked a cloud service.
The obvious reaction to a cluttered view is to just use Shodan, but ASM providers warn against this method, pointing out that it is almost impossible to consider all threats that could harm a company or its market presence. ASM specialists point to their expertise in detecting actively used exploits and often maintain research teams that investigate how threat actors carry out attacks or even infiltrate the dark web scene.
Dealing with Identified Risks
Security expert Richard Werner from Trend Micro distinguishes two types of contingency:
- A risk has been discovered and a decision must be made about how to deal with it.
- The risk has materialized (i.e., an attack is in progress).
Werner emphasizes that according to the NIS2 regulation, corporations need to prepare for both scenarios, because it simply cannot be assumed that all risks have been ruled out. For a long time, security teams used to think of IT security as something like a medieval fortress, with the good guys on the inside, the bad guys on the outside, and the castle wall and moat in between. However, this fortress-style isolation has long since proven to be a deceptive myth – not to mention that the best-known stories suggest that completely eliminating vulnerability is a myth.
According to a study by Trend Micro, an average of 11 percent of assets in companies are highly vulnerable. A security team needs to monitor these assets particularly closely to be able to take action quickly if signs of risk levels rise. The Japanese security provider refers to this approach as "attack surface risk management," which is pretty much the same as ASM.
Functional Scope of ASM
According to KuppingerCole, ASM comprises five areas of responsibility:
- Detecting vulnerable assets
- Creating profiles and evaluating vulnerabilities
- Prioritizing checkpoints on the basis of risk assessment
- Monitoring vulnerabilities on an ongoing basis
- Fixing vulnerabilities – or at least help fix them
The scopes of these five tasks lead to a number of key and auxiliary functions aimed at analyzing, visualizing, monitoring, and, if possible, automatically reducing the attack surface (see the "ASM Functions" box).
ASM Functions
Key ASM functions include:
- Reduction of the attack surface: zero-trust architecture, strong authentication, granular authorization, network segmentation, and interoperability with security tools
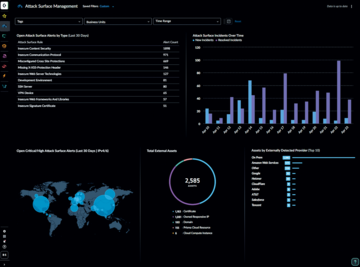
- Visualization of the attack surface: dashboards (Figure 1), mapping to MITRE ATT&CK
- Integration with cyberthreat intelligence (CTI) feeds: aggregation of data from different sources to better understand the attack surface
- Attack surface analysis: aggregation and evaluation of extensive databases, if necessary, with machine learning
- Automated attack surface management: continuous detection, analysis, and monitoring of assets and their vulnerabilities
Supplementary or emerging functions include:
- Cloud: monitor software- and infrastructure-as-a-service (SaaS and IaaS) resources; according to KuppingerCole, state-of-the-art ASM systems are themselves hosted in the cloud
- IoT monitoring, which also includes industrial IoT
- Dark web monitoring: Some ASM vendors have infiltrated dark web forums and attacker groups such as ransomware-as-a-service sites
- Brand protection: monitoring for brand misuse, from DNS manipulation to monitoring social media channels
- DevSecOps integration: ASM should be integrated into DevOps processes at an early stage
- Threat modeling and attack simulation: the use of ASM information to simulate attacks
- Compliance: comparison with legal requirements such as the General Data Protection Regulation (GDPR) or, if applicable, NIS2
How can you separate the wheat from the chaff in the large numbers of ASM offerings around today? According to Strobel, it is a question of what belongs to the corporate network and what does not. Cirosec tested several ASM solutions, some of which performed extremely poorly according to Strobel. One tool did not even correctly map a wildcard for web addresses. As to the number of vulnerabilities a tool finds, established vulnerability engines (e.g., Qualys, Rapid7, and Tenable) are readily available on the market. According to Strobel, however, other tools cover aspects that are less exciting (e.g., websites without an imprint or cookie banners) but can fail to find the genuinely relevant risks.
The core component is always an approach to automated validation of security vulnerabilities that must put IT or security teams in a position to focus on those attack surfaces that a professional attacker would tend to exploit. IBM refers to a Forrester survey, according to which users of the IBM Randori tool require 90 percent less time for vulnerability scans averaged over the year.
ASM specialists such as Google cloud subsidiary Mandiant recommend a comprehensive platform that monitors the dark web, vulnerabilities, and threat data and offers functions to identify and prioritize risks (Figure 2). According to the US provider, up-to-date threat intelligence in particular plays an important role here. Google Cloud's ASM platform combines external resources with Mandiant's front-line threat data to identify the current behavior of relevant threat actors or potential malware continuously.
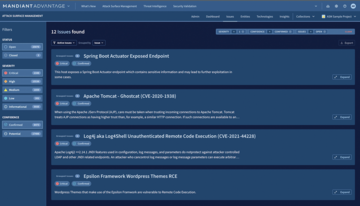 Figure 2: The evaluation of attack surfaces in the context of individual IT environments is a key function of any ASM system. © Google Cloud/Mandiant [5]
Figure 2: The evaluation of attack surfaces in the context of individual IT environments is a key function of any ASM system. © Google Cloud/Mandiant [5]
According to the provider, the prioritization logic considers numerous aspects: shadow IT or unknown systems with their vulnerabilities, misconfigurations of cloud resources, unauthorized developer repositories, suspicious issues such as typosquatting (misuse of typos or word similarities in web addresses), Punycode domains (use of non-ASCII characters in domain names for attack purposes), brand abuse in mobile device apps, web application endpoints, and the security situation of third-party providers.
According to security specialists Group-IB, ASM users set great store by scanning user data; the inclusion of dark web, malware, and leak information in overviews; API and user-defined notification options; and detailed remediation instructions. According to Group-IB, the in-house ASM product follows the user's interest patterns and focuses more or less on specific resources. The idea is to allow the system to assess risks in a dynamic way; that is, determine the relevance of a resource or its threat level for the company on the basis of variable statistical values.
Mandiant emphasizes the value of integration with the user infrastructure to improve transparency, which makes it easier to set priorities and tackle critical security problems effectively.
« Previous 1 2 3 4 Next »
Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.