Photo by Antonio Gabola on Unsplash
A full virtualizer and an alternative to containers
Lighting the Fuse
For many admins, virtualization is "done and dusted": something you can just leave to run on its own. It is all the more surprising when someone comes along with a genuine innovation – or at least new features. Amazon set off fireworks last November, implementing its Firecracker [1] virtualizer under an open source license. Thus far, the tool had mainly been the driving force behind the AWS Lambda service [2], where it enables basic virtualization of small VMs. However, Firecracker can do far more and looks set to conquer territory, even some that is currently occupied by containers.
Technical Underpinnings
Amazon doesn't often publish an in-house solution used in its AWS environment under an open source license. In the case of Firecracker, the approach makes sense, because Firecracker is closely connected to another open source technology: KVM.
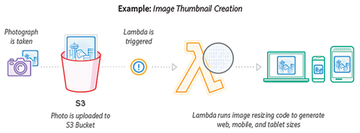
For some time now, Amazon has been offering its Lambda service (Figure 1) as part of AWS, with the aim of providing users with simple virtual machines (VMs) on lean virtual hardware that are significantly cheaper than classic AWS instances.
...Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.