« Previous 1 2
Security with PowerShell 5
Defense Against the Dark Arts
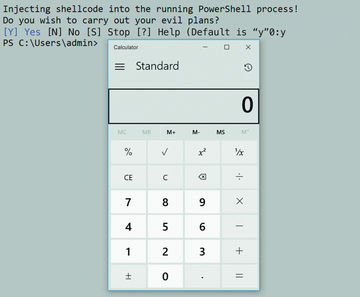
PowerShell has become the ultimate administration tool. However, the scripting language is also enjoying increasing popularity among attackers by allowing them to penetrate systems without detection and work their way up the network (Figure 1). Fortunately, administrators are not completely defenseless, because PowerShell 5 offers some useful security features that both limit the use of the scripting language and block other attack paths.
Windows PowerShell is a powerful tool that combines the command line with a script interpreter. The execution of instructions always linked to the user's context sufficiently arouses the attention of IT security admins; other special features can be viewed critically. Many admins equate PowerShell with the PowerShell.exe file; by simply blocking the executable file, they hope PowerShell will no longer be accessible. However, this is not correct. The following code fragment shows the true nature of PowerShell as part of Microsoft's .NET framework:
$ObjWPS = [POWERSHELL]::Create();
$ObjWPS.AddCommand("get-service");
$ObjWPS.Invoke();PowerShell is stored in the shared library System.Management.Automation.dll, which means that
Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.