Lead Image © sarah maher, 123RF.com
OPNids: Suricata with built-in machine learning
Packet Checker
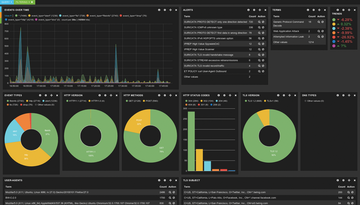
Intrusion detection systems (IDSs) and intrusion prevention systems (IPSs) are some of the classic tools in the administrator's toolbox to counter sophisticated attacks. One popular Linux candidate is the highly functional Suricata [1] (Figure 1).
Various databases house online attack signatures for Suricata, which the tool uses to examine the data traffic and detect attacks. Much like antivirus programs, however, Suricata can only detect attacks with identified signatures. With the progress made in machine learning over the past few years, efforts have been made to generate new signatures automatically with artificial intelligence (AI) and to enter them into Suricata.
In this article, I first look into Suricata in detail and then introduce the Dragonfly machine learning engine (MLE) [2] specifically designed for Suricata. Finally, I look at OPNids [3], a fork of the OPNsense firewall and routing software that integrates Suricata and Dragonfly.
...Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.