
Lead Image © Russell Shively, 123RF.com
A versatile proxy for microservice architectures
Traffic Control
The microservices architecture that has become so popular lately offers a number of benefits, including agile development. If the individual parts of an application no longer have to be squeezed into the release cycle of a large monolithic product, development becomes far more dynamic.
However, if you suddenly have to deal with – from the developers' point of view – many small components, you have to define interfaces that talk to each other. All of a sudden topics such as load balancing, fault tolerance, and security start to play a significant role. Service mesh solutions such as Istio, which I reviewed in an earlier article [1], are currently enjoying great popularity, promising admins an automated approach to networking.
As a closer look at the Istio architecture (Figure 1) reveals, the Envoy open source component is the core of the solution and confers most of the functionality. Fundamentally, Istio is a dynamic configuration framework that feeds Envoy settings for a specific environment.
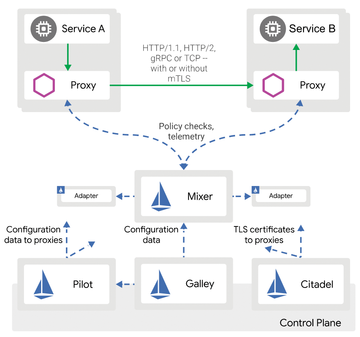 Figure 1: Envoy is the classic tool when it comes to Istio, but it is far more than an Istio add-on. © Mateo Burillo
Figure 1: Envoy is the classic tool when it comes to Istio, but it is far more than an Istio add-on. © Mateo Burillo
Accordingly, the Istio developers refer to Envoy as a sidecar, but if
...Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.





