Photo by Michaela Filipcikova on Unsplash
OpenStack observability with Sovereign Cloud Stack
Guard Duty
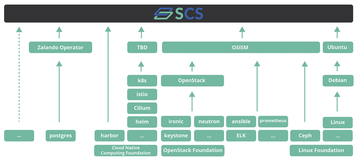
The Open Source Business Alliance (OSBA) Sovereign Cloud Stack (SCS) project was launched in 2019 to enable federation-capable cloud environments. In close collaboration between the community and OSBA's SCS team, the project uses an agile approach to create the appropriate standards and a reference implementation. SCS [1] is an open, federation-capable modular cloud and container platform based on open source software. It builds on proven open source components such as OpenStack and Kubernetes in the reference implementation (Figure 1). As a platform, SCS provides the foundations for creating offerings that deliver full digital sovereignty.
SCS Community
The community comprises a wide variety of cloud service providers (CSPs) and their employees, people from the OpenStack community, and companies working on deliverables that are awarded through open tenders. Collaboration between the different providers creates a level of cooperation that rarely exists elsewhere. Various teams and special interest groups (SIGs) work together on the topics, coordinating standards and requirements
...Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.