
Photo by Jon Tyson on Unsplash
Manage guest accounts in Azure Active Directory
Welcome, Guest
Efficient collaboration while maintaining security standards is often difficult, especially when it comes to the end-user experience. Business-to-business (B2B) transactions are made in the cloud, but the cloud itself is a dangerous place. Passwords should not be accepted as the only credential, and multifactor authentication (MFA) should be the standard. In this context, it is less than useful that the MFA status is – thus far – only valid within the boundaries of the tenant and that other tenants are not trusted. If two communication partners are committed to a modern work approach with zero trust, things become even more difficult: The device status cannot be transferred either.
New Possibilities with xTAS
Cross-tenant access settings (xTAS) offer an opportunity to improve this situation. The feature is designed to control collaboration fully across tenant boundaries and let organizations control inbound and outbound collaboration by defining tenant-wide and partner-specific rules (Figure 1).
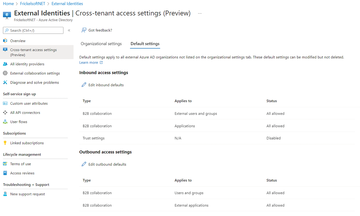 Figure 1: The default settings for cross-tenant access for B2B collaboration give you free rein. If so desired, you can establish more granular
Figure 1: The default settings for cross-tenant access for B2B collaboration give you free rein. If so desired, you can establish more granularBuy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.






