Photo by Tobias Tullius on Unsplash
Monitoring changes in Active Directory with built-in tools
Tracking Down Attackers
For some initial, crucial findings in Windows during incident and event management, you do not need to look further than the existing Event Viewer logs. After the introduction of Windows Server 2008 and Vista, Microsoft established a more granular approach. The events are sorted into categories along with subcategories for improved monitoring and recording. Typing
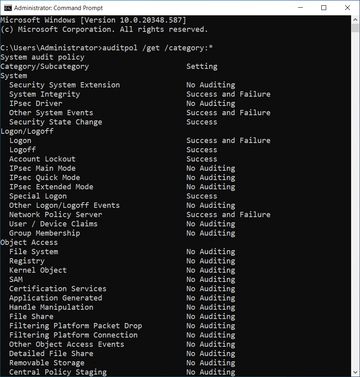
auditpol /list /subcategory:* auditpol /get /category:*
at the command line lists a quick overview of the possibilities and shows the current configuration (Figure 1).
You will usually control the Advanced Audit Policy Configuration settings with a group policy; you can also set it up at the command line. If you want the configuration to be used, it needs to be enabled. On newly installed systems, the correct value is set by default and does not need to be defined explicitly. However, best practices dictate activating this value with group policy for safety's sake. The reason lies in the legacy Active Directory (AD) installed on Windows Server 2000/2003, whose Default Domain Controllers Policy has never been edited or still uses the obsolete monitoring policy. You can reset the
...Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.