Harden services with systemd
A Hard Nut to Crack
One of the most important goals in the development of systemd is securing Linux. Of course, you can only improve what can be measured, which is why Galileo Galilei advised: "Measure what is measurable, and make measurable what is not." Following this maxim, systemd now makes system security under Linux measurable and improvable.
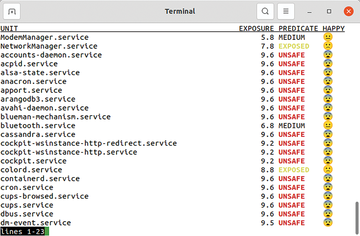
More specifically, it is the systemd-analyze security command that allows this measurement. When executed, it returns a table like that shown in Figure 1, listing each service managed by systemd (UNIT
); a numerical value for the degree of protection (EXPOSURE
, where 10 is both the highest and worst value); a verbal translation of this value (PREDICATE
); and another version of the rating (HAPPY
) in the form of an emoji.
Additionally, systemd-analyze can reveal how it arrives at its assessment: To see this, start it with the name of a service unit. As shown in Figure 2, it lists all the factors that have been checked, along with a checkmark for passed or an X for failed.
Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.