Lead Image © Maxim Kazmin, 123RF.com
Segmenting networks with VLANs
Logically Tunneled
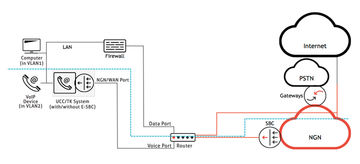
The most obvious network separation is routinely carried out between the Internet and the internal network. The connection of the IT infrastructure of a company to the outside world is typically implemented in a demilitarized zone (DMZ), which is a subnet that provides controlled access to public servers and services that exist in it. A firewall separates the Internet from the DMZ, and another firewall separates the DMZ from the internal network (Figure 1). Thanks to this separation, access to publicly accessible services, such as email, Internet, DNS, or voice over IP (VoIP), can be granted while still protecting the internal corporate network from unauthorized access from the outside. Also, the distribution of the data streams into virtual LANs (VLANs) takes place in the DMZ.
If you use VoIP, the Enterprise Session Border Controllers (E-SBCs) are also installed in the DMZ. This is a kind of Session Initiation Protocol (SIP) firewall. The data firewalls pass the VoIP/video streams to the E-SBC via an open port. Because the E-SBC is an application-specific test component, it performs "deep packet inspection" and ensures that only legitimate SIP messages reach the VoIP/video components in the corresponding voice
...Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.