Wireshark
Linux comes with a lot of useful network analysis tools, many of which provide excellent results that can easily compete with commercial tools. Despite this, Windows administrators are sometimes wary of deploying open source tools without a graphical user interface.
Basically, network analysis software does nothing but record all the traffic on the specified network interface. To allow this to happen, software continuously grabs all of the data packets and stores them on disk. Then, the software decodes the data and displays the results on screen.
Tcpdump is a classic tool in the Unix world and is widely used by experts. However, it only offers a command-line interface. Tcpdump is available for just about any Unix derivative, such as AIX, BSD, Solaris, and is nearly always included in the standard package sources of any version of Linux, if not installed by default. A port for Windows exists under the name of WinDump, based on WinPcap. Tcpdump needs direct access to the hardware and thus typically runs with root privileges. The exceptions are Mac OS X and Solaris, where the user only needs access privileges for the network interface card device file.
By default, Tcpdump reads all the data that reached the specified network card across the network and displays it, for example, on the standard output device, or stores it in files that the administrator can evaluate later. One particularly impressive thing about Tcpdump is its useful collection of filters. These capture filters are based on Libpcap, a C/C++ library that supports access to the network interface’s link layer. Administrators can control Tcpdump’s behavior at the command line by passing in parameters, including the filters to use.
Ethereal and Wireshark
Because a command-line interface isn’t everybody’s idea of user friendliness, graphical solutions that also rely on the Libpcap library have been around for some time. One of these tools is Wireshark, which dates back to 2006. It was formerly known as Ethereal and is probably known to many administrators by that name. The tool was renamed when version 0.99.1 of Wireshark was released, because Ethereal developer Gerald Combs left Ethereal Software. He launched a successor project under the name of Wireshark with CACE Technologies, and this prompted Ethereal Software to discontinue the development of the predecessor product.
Today, Wireshark is mainly developed by the Wireshark community. Ethereal and Wireshark are genuine open source projects, although Ethereal is oriented to network analysis products by commercial vendors. Development milestones for Wireshark include version 1.0, which became available in March 2008, and the bug fix version 1.4, which became available in the summer of 2008. Both of these versions offered experimental support for Python scripts and the ability to right-click the packet details in the packet list to add protocol fields.
The release of Libpcap 1.0.0 added the ability to define the buffer size for recording and to view JPG files directly in Wireshark. Version 1.6 of Wireshark (which prompted me to write this article) was released in July 2011 and offers better support for large files of more than 2GB. It can also import text dumps in a similar style to text2pcap. The developers have also made the GUI more user-friendly so that admins can hide columns while at the same time defining custom columns for the required fields.
The main feature of the new version is support for more than 30 new protocols including JSON, Wi-Fi P2P (Wi-Fi Direct), and Fibre Channel over InfiniBand. Also, Wireshark 1.6.0 can export SSL keys and SMB objects. Another new feature in Wireshark 1.6 is that the software displays VLAN tags (IEEE 802.1q) directly in the Ethernet II protocol tree.
Wireshark is licensed under the GPLv2 and can be installed using the package manager of just about any popular Linux distribution. However, Ubuntu Natty comes with Wireshark version 1.4.6. You can check out the download page for the source code of the current version for Unix systems and binary packages for Windows and (as of 1.6) Mac OS X. Installing the 32-bit Windows version is self-explanatory. You just need to download the archive and then double-click the installer file (wireshark‑win32‑1.6.1.exe ). The Wireshark installation wizard also launches a helper for installing WinPcap, which needs to complete first.
Wireshark Basics
Before you start analyzing your network with Wireshark, it is always a good idea to do some planning. Of course, this approach applies to the use of any system tool, but, in the case of network analysis with gigabit Ethernet, you really do need to make sure that you have sufficient system resources. For this reason, administrators should have some idea of the volume of data to expect. This factor will depend on the kind of data traffic you want to capture and with what objective, which, in turn, will drive your choice of filters. You may also need to ensure that this doesn’t influence the measurement because it, for example, automatically discards some packets.
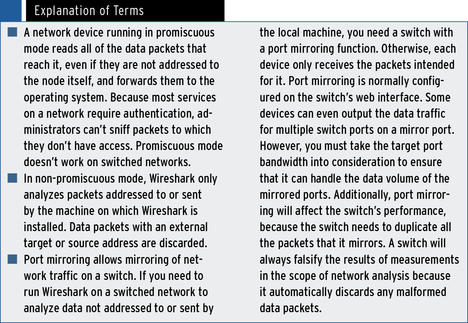
If you need to measure network data that is not intended for the host in which the network interface is configured, the Wireshark configuration dialog gives you the option of running the network device in promiscuous mode or non-promiscuous mode. In non-promiscuous mode, Wireshark will analyze only packets sent to or from its own host, and it will discard all other data packets (with external target addresses.)
In promiscuous mode, Wireshark can analyze any data packet from any machine that exists on the network because it will also accept data packets with external target addresses in this mode. If all of the resources on the network are connected by means of hubs, using promiscuous mode to read all of the data packets isn’t a problem, because hubs always send all data packets to all ports.
However, switches are very popular even on small networks, not to mention enterprise networks. The idea behind a switched network is to declutter the data traffic so that a node attached to a switch only receives data packets intended for it. Thus, it makes sense to use the port mirror function on a switched network to route the mirrored port data (for the node you want to analyze) to the network card in the local machine on which Wireshark is installed. For more details, see the “Explanation of Terms” box.
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.