
Lead Image © Davorr, Fotolia.com
Workspace ONE for endpoint management
Empowered
The trend is moving away from stationary and toward mobile workplaces. That said, it is still important for the IT department to manage all end devices efficiently. Because of all the different operating systems, a clear-cut tool for endpoint management is essential. VMware's Workspace ONE [1] aims to integrate all of a company's devices, including devices belonging to employees (bring-your-own-devices, BYODs), uniformly and centrally into the existing infrastructure with the help of a secure platform. The overriding goal is to organize application lifecycle management. The overall strategy is known as Unified Endpoint Management (UEM) and is one of the two core components of Workspace ONE.
In addition to UEM, the second core component, Workspace ONE Access, combines the administration of users and user groups, the assignment of access authorizations to the applications, and the setup and provisioning of virtual desktops with the respective applications in a catalog (Figure 1). The Access component provides a connector to other identity (ID) providers such as Ping, Okta, and Microsoft Azure, providing a common catalog interface for all applications. The AirWatch Cloud Connector, in turn, securely transmits requests from Workspace ONE UEM to the back-end infrastructure. Table 1 provides an overview of all components of Workspace ONE.
Table 1
Workspace ONE Components
| Component | Function |
|---|---|
| VMware Workspace ONE UEM | Enterprise mobility management |
| VMware Workspace ONE Access | Identity platform |
| VMware Workspace ONE Intelligence | App analysis and automation |
| Workspace ONE App | User access to apps |
| VMware Horizon | Virtual desktops and remote desktop services (RDS) |
| VMware Workspace ONE Boxer | Secure email client |
| VMware Workspace ONE Browser | Secure web browser |
| VMware Workspace ONE Content | Mobile repository for content |
| VMware Workspace ONE Tunnel | App VPN access to enterprise resources |
| VMware AirWatch Cloud Connector and VMware Identity Manager Connector | Synchronization with enterprise directories |
| VMware Unified Access Gateway | Gateway for secure Edge services |
| VMware Workspace ONE Secure Email Gateway | Email proxy server |
| Certificate Authority Integration | Lifecycle management of provided certificates |
| VMware Email Notification Service | Email messaging for Workspace ONE Boxer on iOS |
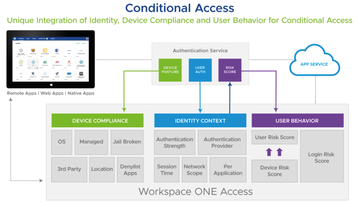 Figure 1: Managing user access with Workspace ONE Access involves various modules. Image courtesy VMware. [2]
Figure 1: Managing user access with Workspace ONE Access involves various modules. Image courtesy VMware. [2]
Architecture and Services
Administrators use Workspace ONE to define user groups, policy settings, and device configurations. Users then access their applications through Workspace ONE according to the defined settings and configurations. Figure 2 illustrates the interaction of the various components and interfaces in Workspace ONE.
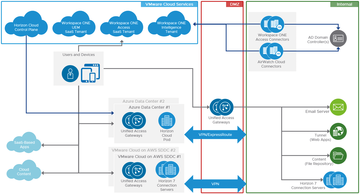 Figure 2: A schematic overview of Workspace ONE shows the interplay of the numerous components and interfaces. Image courtesy VMware. [3]
Figure 2: A schematic overview of Workspace ONE shows the interplay of the numerous components and interfaces. Image courtesy VMware. [3]
Workspace ONE services are based on the integration of VMware Workspace ONE UEM, Workspace ONE Access, and VMware Horizon. Deployment can be achieved in a variety of configurations, including:
- On-premises deployment of Workspace ONE Access and Workspace ONE UEM.
- Cloud-based deployments of Workspace ONE Access and Workspace ONE UEM.
- Hybrid deployments with different components available either on-premises or in the cloud.
Basic EMM Features
As mentioned earlier, administrators can deploy, manage, and secure applications with Workspace ONE. In doing so, IT can leverage interfaces for diverse operating systems to configure mobile devices such as notebooks, smartphones, and tablets in line with corporate policies. Workspace ONE's UEM accesses enterprise mobile management (EMM) interfaces to provision, configure, and secure applications and devices. This level of control enables IT to implement a flexible BYOD program that lets users choose their devices.
In this context, EMM is an umbrella term for systems that manage mobile devices in the enterprise. It is subdivided into the following subareas:
- Mobile device management (MDM): Manages mobile devices with software and hardware as specified by the enterprise.
- Mobile application management (MAM): Manages the software installed on mobile devices through an internal company app store.
- Mobile content management (MCM): Provisions the company's own applications and enables files and documents to be passed on to colleagues, business partners, and customers by the mobile route.
Profiles and Software Distribution
The use of device profiles changes the behavior of enrolled devices. Device profiles, combined with compliance policies, help enforce corporate rules and procedures. For example, Workspace ONE UEM device profiles can be created on the basis of criteria such as users, groups, platforms, and operating systems. You can also create smart groups, which are customizable groups that allow you to filter dynamically.
User groups can control the assignment of access authorizations individually on the respective devices. Workspace ONE UEM lets you create device-specific profiles for the individual operating systems. The functions are adjustable to suit requirements, which means you can activate or deactivate one or more functions, such as switching off the Siri voice assistant on Apple devices.
However, profiles need to be set up categorically and in a granular way. This approach simplifies the management of individual profiles. As a result, they are not valid for all devices but, instead, are specifically for the selected operating system in the matching smart group. Device registration establishes the initial communication with Workspace ONE UEM to enable EMM.
Another component of UEM is data leakage protection. Examples of potential data leaks include saving work documents to a public storage device such as Dropbox or receiving work email with an unmanaged email client. Other security measures include encrypting and restricting email traffic, such as editing and sharing attached files. The company can also require that only applications provided by the enterprise are used instead of OS-native applications. The choice of browser can also be restricted for users to ensure secure browsing.
Workspace ONE lets you integrate existing ID providers, such as Microsoft's Active Directory or another LDAP-based directory, to implement user synchronization, authentication, and application access. Finally, the tool enables simplified software distribution. Deploying, updating, and deleting software packages can all be automated. Moreover, you can distribute the packages in predefined time windows and as a function of the network infrastructure load, and notifications for upcoming software updates lets users prepare for them accordingly.
Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.






