BlackHat USA 2010
Learning from the Best
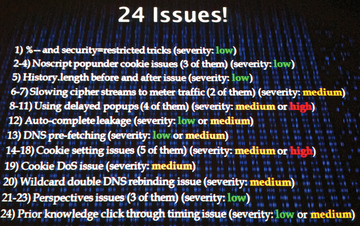
I've been to BlackHat twice now, and both times I have taken the same lesson home: If you think things are getting better in the field of computer security, you're probably wrong. Over the years, progress has been made identifying bug types – currently the CWE lists 668 weaknesses in 120 categories – and some progress has been made with projects to identify and remove them systematically (e.g., OpenBSD has had remarkable success). However, you then come to the BlackHat conference and see a presentation like "HTTPS Can Byte Me," in which Robert Hansen and Josh Sokol disclosed 24 vulnerabilities (Figure 1) that can compromise the integrity and security of SSL-encrypted web traffic [2].
The problem is not so much a failing within SSL, but unless you're taking extreme measures to protect network traffic against analysis (e.g., padding traffic out, introducing time delays, etc.), chances are, attackers will be able to glean information even if they can't read the traffic directly.
Also, consider the case of the well-meaning web browser that attempts to be helpful. I guess people hate typing in personal information, so almost all browsers support "auto-complete," which automatically fills out form fields (e.g., name,
...Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.