
Andrii IURLOV, 123RF.com
Targeted defense against brute force attacks
Goalkeeper
To protect your system, sshguard takes a simple and effective approach, similar to that of a small intrusion detection system. The tool continually monitors logfiles for selected services. If it discovers questionable network access, it temporarily blocks the presumed attacker by introducing firewall rules (Figure 1).
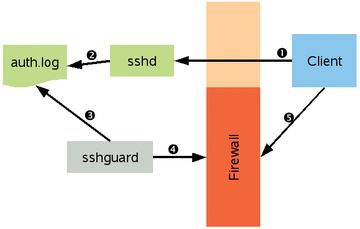 Figure 1: The SSH daemon logs client requests (1) in the auth.log file (2). Then sshguard (3) monitors the file and creates a firewall rule (4) that blocks the client (5) if it notices to many login attempts.
Figure 1: The SSH daemon logs client requests (1) in the auth.log file (2). Then sshguard (3) monitors the file and creates a firewall rule (4) that blocks the client (5) if it notices to many login attempts.
If the attacker doesn't stop at this point, sshguard will block the connection for increasingly long periods. This intelligent strategy has the advantage of not accidentally locking out forgetful users, and it provides effective protection against automated password crackers.
The Usual Suspects
As the name suggests, sshguard was originally designed to monitor failed SSH login attempts. But now, it can help you with any of the services listed in the "Supported Services" box. For other services, you can send attack patterns to the developers on a
...Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.






