
© monophoto, 123RF.com
Effective honeypots with sensors on production systems
Trapped!
Individual sources report that more than 286 million new, positively identified malware instances were registered in 2010 alone [1], not counting unreported cases (i.e., malware that cannot be detected by current security tools). In many cases, these huge numbers of "new" malicious programs (Figure 1) are not necessarily malware with any new functionality; instead, they are often the result of polymorphic or metamorphic code that regularly generates slightly modified variants of a malicious program with virtually identical functionality. The objective of this procedure is to modify the structure of the malware so that it is no longer recognized by classic, signature-based detection tools.
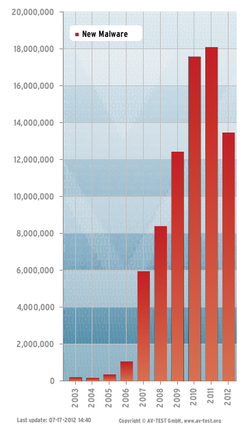 Figure 1: The number of malicious programs on the Internet has exploded in recent years. (From AV-TEST Institute [2], which registered more than 55,000 malicious programs every day.)
Figure 1: The number of malicious programs on the Internet has exploded in recent years. (From AV-TEST Institute [2], which registered more than 55,000 malicious programs every day.)
Although regular updates of signature databases used in virus scanners and intrusion detection systems are essential, uniquely assigning all newly discovered malware to a signature would take an average of 38 new signatures per minute. This number
...Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.






