
Lead Image © jaroonrat vitoosuwan , 123RF.com
Verifying packages with Debian's ReproducibleBuilds
Identical Build
Open source software offers a big security benefit: Unlike proprietary software, anyone can view the source code, so in theory you know what you are installing. However, the overwhelming majority of users install prebuilt software packages provided by their Linux distributors. These users rely on system developers and package maintainers to ensure that the binary packages do not contain malicious code that deviates from the official source code.
The Debian ReproducibleBuilds project helps you verify that the package matches the source code and that no flaws have been introduced (Figure 1) [1].
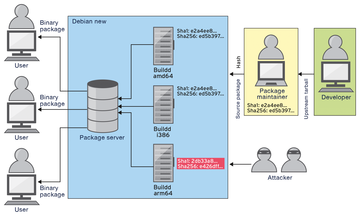 Figure 1: If the build system is compromised, the binary package produced by it in the ReproducibleBuilds system has a different hash value (red entry).
Figure 1: If the build system is compromised, the binary package produced by it in the ReproducibleBuilds system has a different hash value (red entry).
Attack Scenarios
As a popular Linux distribution, Debian distributes its own software to a large number of users worldwide. The customers are not only private users, but also organizations, research institutions, and companies. This complex and decentralized software distribution system creates opportunities for attackers to foist malicious code onto
...Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.





