Lead Image © Joellen Armstrong, Fotolia.com
Understanding the Spanning Tree protocol family
Switch Keeper
The Spanning Tree protocol, which was designed to provide a loop-free Ethernet network topology, has been around for more than 30 years and has been through many iterations. The various versions include the conventional Spanning Tree protocol, Per-VLAN Spanning Tree protocol, Rapid Spanning Tree protocol, and a more recent version known as the Multiple Spanning Tree protocol. This introduction to Spanning Tree looks at some of the important enhancements introduced with later variants.
Broadcast Storm
Ethernet uses a multiaccess broadcast technique. A switch spreads the broadcast message all over the network to make sure all hosts can receive the message. To accomplish the task, when the switch receives a broadcast, it duplicates the message to all ports except the port that sends the broadcast.
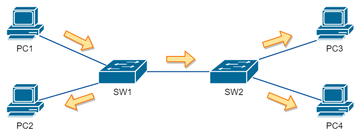
In Figure 1, PC1 generates broadcast traffic. When SW1 receives the traffic, it duplicates to all other ports. SW2 does the same thing, so that all hosts in the network receive the broadcast message. This mechanism works perfectly in a simple network that does not have a loop connection.
A loop connection complicates the simple scenario depicted in Figure 1. In
...Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.