« Previous 1 2 3
Call web pages in the terminal with Browsh
Block Graphics
A graphical user interface is not always available (e.g., when working with secure shell (SSH) on a remote server), and in some areas, data merely drips from the Internet. If you want to save bandwidth or work at the command line, you will appreciate a pure text browser. Browsh takes this one step further and even converts images and videos into characters. For this to work, the browser relies on a well-known friend in the background: Firefox.
Shell Fan
Many Linux users prefer the command line to a graphical user interface. If you are a die-hard shell fan and want to look up something on the Internet, web browsers like the classic Lynx that only deliver plain text on a page can help – and save bandwidth in the process. However, you lose the layout and images.
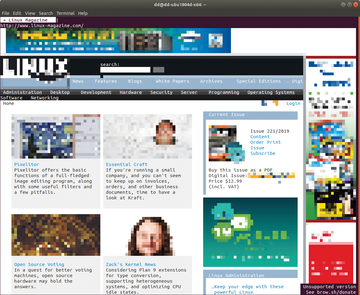
A modern text browser composes a web page completely from text characters [1], keeping the layout to a large extent. The software even tries to display graphics and animation consisting of individual color blocks (Figure 1). In many cases, you can at least guess the appearance of the graphic.
...Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.