« Previous 1 2 3 4 Next »
IPv6 Tables
Creating Firewall Rules with ip6tables
IPv6 does away with NAT, which functions much like a firewall for internal networks with IPv4, even though it was not designed for that purpose. With IPv6, a dedicated firewall now needs to provide protection against attacks from the Internet and other networks. Linux has the ip6tables tool for this purpose. In this article, I develop a basic set of rules.
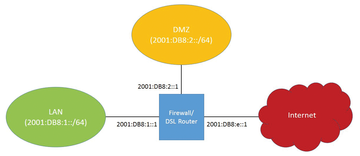
The underlying scenario for this article involves a DSL router with Linux (Figure 1), which is required on the one hand to protect internal systems from attacks from the Internet and, on the other hand, to provide access to an internal server connecting to a DMZ interface. The aim is to manage both the end-to-end IPv6 network traffic and to control access to the router itself.
The router must be accessible for administrative purposes, at least using SSH and HTTPS, and it needs to act as a DNS server for the internal systems.
Since Linux kernel version 2.6.20, ip6tables has supported stateful inspection, wherein the firewall automatically assigns response packets to a communication channel and allows communication where appropriate. This function, which is now common on almost all firewall platforms, reduces both the scope and the complexity of the rules significantly.
Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.