« Previous 1 2 3 Next »
Integrating a Linux system with Active Directory
Gardening
Time Synchronization
Active Directory uses the Kerberos protocol for authentication purposes. However, this protocol is sensitive to clock timings between systems collaborating in a Kerberos domain. Consequently, if the time difference between the Ubuntu system and the Active Directory controller is more than five minutes, authentication against the Active Directory controller will ultimately fail [3].
Primarily, Unix and Linux systems use the Network Time Protocol (NTP) for time synchronization (e.g., Ubuntu uses the default NTP server at ntp.ubuntu.com ). No timing differences can exist between the Ubuntu machine and the Active Directory controller, so you can't use an external timing source.
To configure the Ubuntu machine to use the Active Directory controller as its NTP server, install and configure a service like NTP or chrony. If everything has been set up correctly, enter
$ ping example.com $ ping WIN-2RIFAMT88GR.example.com
to make sure the Ubuntu machine can now ping the domain name and the Active Directory FQDN.
Discovering a Domain
The realmd system D-Bus service manages discovery and registration in realms, such as Active Directory domains. To install the package and check the members already enrolled or registered with the Active Directory domain, enter
$ sudo apt install realmd $ realm list
An empty result shows that no machines are enrolled so far. Now discover your domain (example.com here) by running the command
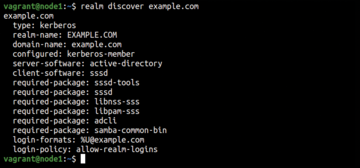
$ realm discover example.com
After successfully discovering the domain, you'll see output similar to that shown in Listing 1. Interestingly, the result also lists the requisite and most appropriate packages for joining the domain. The command
Listing 1
Discovering the Domain
vagrant@node1: $ realm discover example.com example.com type: kerberos realm-name: EXAMPLE.COM domain-name: example.com configured: no server-software: active-directory client-software: sssd required-package: sssd-tools required-package: sssd required-package: libnss-sss required-package: libpam-sss required-package: adcli required-package: samba-common-bin
$ sudo apt install sssd sssd-tools libnss-sss libpam-sss adcli samba-common-bin
installs those packages.
Joining a Domain
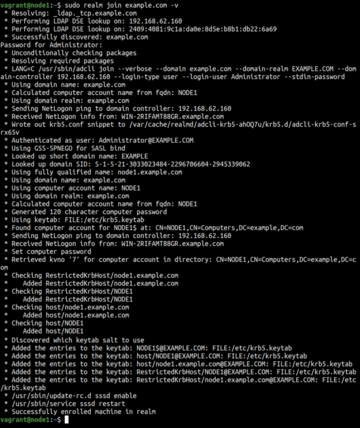
The configured: no option shown in Listing 1 indicates that the system isn't ready to join the Active Directory domain. To do so, you can simply run the realm join command (Figure 2):
$ sudo realm join example.com -v
A second realm discover command shows the change (Figure 3).
The default approach of realm is to log in from the domain administrator's account. However, you can use the -U switch to pass a different username [4]. The -v option provides verbose output.
Additionally, the realm tool also creates a configuration for the SSSD and adds modules for PAM and NSS. Furthermore, it has taken care of starting the required services. You can also check the /etc/sssd/sssd.conf<file> file (Listing 2):
Listing 2
Checking sssd.conf
vagrant@node1: $ sudo cat /etc/sssd/sssd.conf [sssd] domains = example.com config_file_version = 2 services = nss, pam [domain/example.com] default_shell = /bin/bash krb5_store_password_if_offline = True cache_credentials = True krb5_realm = EXAMPLE.COM realmd_tags = manages-system joined-with-adcli id_provider = ad fallback_homedir = /home/%u@%d ad_domain = example.com use_fully_qualified_names = True ldap_id_mapping = True access_provider = ad
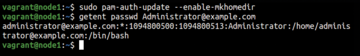
Moving on, you need to create a home directory for every AD user that will log on to the Ubuntu machine. To set up pam_mkhomedir, run the command (Figure 4)
$ sudo pam-auth-update --enable mkhomedir
Additionally, you can fetch the details of an AD user with the command
$ getent passwd Administrator@example.com
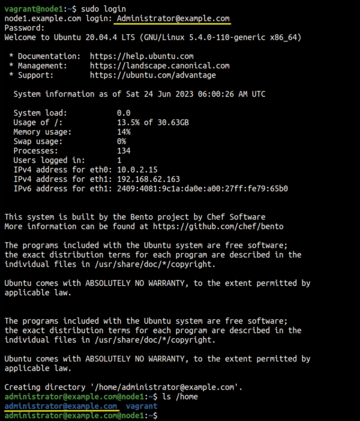
At last, you can log in on the Ubuntu machine with the credentials of the Active Directive user and verify that you get the user home directory on the Ubuntu machine with the commands
$ sudo login $ ls /home/
The login command prompts you to supply the username (appended with the domain name) and password (Figure 5).
« Previous 1 2 3 Next »
Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.