Linux Essentials for Windows Admins – Basics
Years ago, I taught an introductory Unix class to eager Microsoft Certified Solutions Expert (MCSE) students who invariably asked the same question in every class: “Why do I have to take a Unix class when I’m working on my MCSE?” My answer was a lengthy explanation of the origins of Unix, DOS, and Windows that ended with, “… and, because real environments are mixed. Few companies, of any size or complexity, run a single operating system.” It was true in 1996 and it’s true today.
The larger and more complex a company network, the more heterogeneous it’s likely to be. You could encounter Solaris, HP-UX, AIX, Linux, and other non-Microsoft operating systems (OSs). In larger companies, it’s also true that jobs have a tendency to be “compartmentalized.” You will have a group that only works with Unix, another that only works on switches and routers, and one that only administers Windows systems.
However, it’s not only wise to learn some Unix basics, in some shops, it’s required. For example, a few days ago, a friend forwarded me a Windows Administrator job opening that listed the following as primary requirements:
- Windows
- System administration of SQL database
- NetBackup
- VMware
- Linux experience and working with networks a definite plus
Notice from the description that Windows is but one of the skills required or strongly desired for this position. As a Windows administrator, you need to know more than Windows; you need a complete 360-degree view of how computers and networks function. The Windows operating system is but one component of the larger picture.
You don’t have to be a router expert to understand routing, nor do you have to be a Unix nerd to understand basic navigation, normal operation, and minor troubleshooting. You need to acquire the necessary training to assess problems, to provide some support, and to know when to call for higher level technical assistance. The purpose of this series is to provide Windows admins with the necessary Unix skills to accomplish those goals.
Learning Unix via Linux is an excellent way to gain experience without jeopardizing production systems. It also gives you the opportunity to administer a Unix system, as well as participate as a user.
During this series, I will give you direct comparisons between Linux and Windows so that you can see how similar the two operating systems are. Types of comparisons are analogous commands, analogous functionality, and analogous configuration.
Unix Security Information
Like Windows, Unix has two primary user security levels: User and Administrator. The administrative user on Unix systems is the root user. It is the local administrator for a system. Unix is a system of least privilege. That is to say that Unix only provides users with the privileges necessary to perform user-related tasks.
Users may navigate the filesystem, issue system commands, and connect to other systems via TCP/IP utilities. Users do not have the ability to reboot a system, view secure files, or change system files.
File security is simple. All files have User, Group, and Other ownership permissions or privileges associated with them. Each of those entities (User, Group, and Other) may have read, write, or execute permission on a file.
User Group Other
rwx rwx rwx
For example, a file that you create in your home directory has the base permission rw-r--r-- . The system grants this basic security with something known in the Unix world as the user mask, or umask . Certain privileges, or modes , are masked from the file when created. The execute bit, x , is never granted to a file by default, so any new file you create will have the permission rw-r--r-- . The umask is a system setting and passes to all users.
The execute bit must be set explicitly on files. As you might have guessed, the execute bit, x , allows the user to execute a file that carries that privilege.
By default, files you create have read/write privilege for the user (Owner), read-only privilege for the Group, and read-only privilege for Other. Other is anyone outside of the file’s owner or group. Other is often referred to as World in Unix parlance. You’ll often hear Unix folk talk about files that are “World readable.” They are talking about that r privilege in the Other group location.
Note that I mentioned, read-only, as a privilege. When speaking of read-only files, you now know the derivation of the term – the file has read permission only. An example of a file that has read-only privileges for everyone has permissions r--r--r-- .
In Unix, file permissions are also assigned numbers: r = 4 , w = 2 , and x = 1 . For any file you create, that file has a permission value of 644 (rw (6 )-r (4 )--r (4 )-- ). What is the permission value of a file that has the following permissions?
rwxrw-r--
The correct answer is 764 . What about for the read-only file (r--r--r-- ) for everyone mentioned earlier? If you answered 444 , you’re correct. You’ll never see the permission values on actual files. Those numbers are a shortcut way to speak about file permissions and to understand permission from a strictly numeric point of view.
When you view a file list, you’ll only see the letters. For example, here are a few files from my home directory:
drwxr-xr-x 2 khess khess 4096 2012-07-03 15:59 Desktop drwxr-xr-x 2 khess khess 4096 2012-07-03 15:58 Documents -rw-r--r-- 1 root root 0 2012-07-07 15:04 goo.txt drwxr-xr-x 2 khess khess 4096 2012-07-03 15:58 Music -rw-r--r-- 1 khess khess 0 2012-07-07 14:55 newbie.txt drwxr-xr-x 2 khess khess 4096 2012-07-03 15:58 Pictures drwxr-xr-x 2 khess khess 4096 2012-07-03 15:58 Public drwxr-xr-x 2 khess khess 4096 2012-07-03 15:58 Templates drwxr-xr-x 2 khess khess 4096 2012-07-03 15:58 Videos
Notice the files newbie.txt and goo.txt have file permissions rw-r--r-- .
Directories (folders) in Unix are also files. Can you determine which files in the listing above are directories? Note that directories have a d bit before the file permissions. From this listing, you can also see the name of a file’s User and Group owner. Other isn’t listed because it’s unnecessary to do so.
You’ll also note that, because they’re files, directories have permissions associated with them. The execute bit, x , on a directory means you’re able to cd into that directory. If you’re familiar with DOS or the Windows command line, you realize that cd is the Change Directory command. It works similarly in Unix and in Windows.
Analogous Commands
Leaving file permissions and security until later in the series, it’s time to explore commands that have similar names and functions between the two operating systems. For clarity, Windows command-line commands are shown in UPPERcase and Unix commands are shown in lowercase.
| Table 1: Windows Commands and Equivalent Unix Commands | ||
| Command | Windows | Unix |
| Directory list | DIR | ls |
| Change directory | CD | cd |
| Make directory | MD | mkdir |
| Remove Directory | RD | rmdir |
| Delete | DEL | rm |
| Echo | ECHO | echo |
| Display file contents | TYPE | cat |
| Copy a file | COPY | cp |
| Move a file | MOVE | mv |
| Rename a file | REN | mv |
| Display current user | WHOAMI | whoami |
| Locate file | WHERE | whereis |
| List running processes | TASKLIST | ps -ef |
| Recursive copy | XCOPY | cp -R |
| Display date | DATE | date |
| Display time | TIME | date |
| Sort file contents | SORT | sort |
| Display current directory | CD | pwd |
| Display environment variables | SET | set or env |
| Wait for x seconds | SLEEP x | sleep x |
| Run command with elevated privileges | RUNAS | sudo |
| Show PATH | PATH | echo $PATH |
| List open files | OPENFILES | lsof |
| Display IP address info | IPCONFIG | ifconfig |
| Search for a string in a file | FIND | grep |
| Change file attributes | ATTRIB | chmod |
| Filesystem check/diagnostics | CHKDSK | fsck |
Other commands for TCP/IP connectivity are exactly the same for both operating systems, such as telnet , ftp , ssh , ping , and nslookup . Remember that most Unix commands use lowercase only and Windows commands are case insensitive.
The Unix Filesystem
Now that you’ve had a short introduction to file security and comparable commands, it’s time to log in to a Unix system and learn some command-line basics. Windows users and administrators shun the command line, but smart administrators embrace it. If you’ve read my PowerShell series, you know that PowerShell is a powerful, command-based scripting language. You have that same power in Unix. You can run commands one by one, stack them into a pseudo-script, or create a file containing various commands much as you would a .CMD or batch file. For now, I’ll stick with using commands one at a time.
If you have a Linux or Unix system handy, try these commands for yourself. You can also try their analogs at a Windows command prompt for comparison.
Log in to your Unix system either locally or remotely and open a Terminal window. Most Unix server systems don’t have a Window manager or graphical desktop installed, so you might already be at a command line as soon as you log in. Also note the difference between log in and log on: Unix users log in to their systems, whereas Windows users log on. It’s the same process but different terminology.
Your command prompt will probably look something like: $ or user@host:~$ , or bash> $ . It doesn’t really matter what it looks like as long as you’re logged in with a regular user account. The $ symbol typically means you’re logged in as a regular user. The root user has a # prompt. This subtle difference helps Unix administrators avoid making costly and devastating mistakes, such as accidentally removing critical system files and directories.
You see, unlike Windows, the Unix operating system assumes that, when you issue the rm command on a file, you really want to remove it. There’s no, “Are you sure?,” “That’s a critical system file,” or even a “File in use” warning. If you issue the rm command for the system’s password file as the root user, it’s removed and you can’t undelete it. To undelete files, you’ll need a third-party application.
So, the two basic rules are:
- Do everything you can do as a regular user and perform root user functions using sudo (RunAs ).
- Always make a backup copy of any system file you edit.
Working in the Unix shell feels very similar to working at the Windows command line. Once you log in, you’re placed in your home directory, which is named with your user account name and located within the top-level directory, /home . For example, my home directory is /home/khess . Check your Windows system for your default “home” location. It’s likely to be, C:\Users\USERNAME . Again, both OSs have a very similar structure and conventions.
You probably noticed one small difference between the two systems in how you refer to directories and subdirectories. Unix has no drive letters. Windows users expect to see C: , D: , E: , and so on, but in Unix, you only refer to directories off of the root directory. The root directory has nothing to do with the root user. The root directory is the topmost directory in its hierarchical filesystem (Windows is also hierarchical).
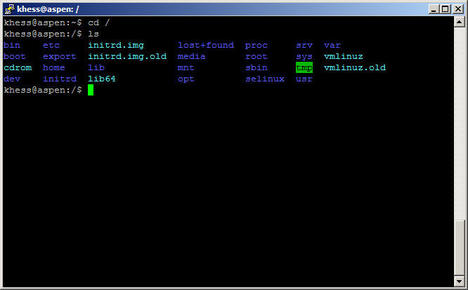
To view your Unix filesystem’s top-level directories, enter the following commands, as shown in Figure 1, pressing the Enter key at the end of each line:
cd / ls
Not all Unix systems show files and directories in color.
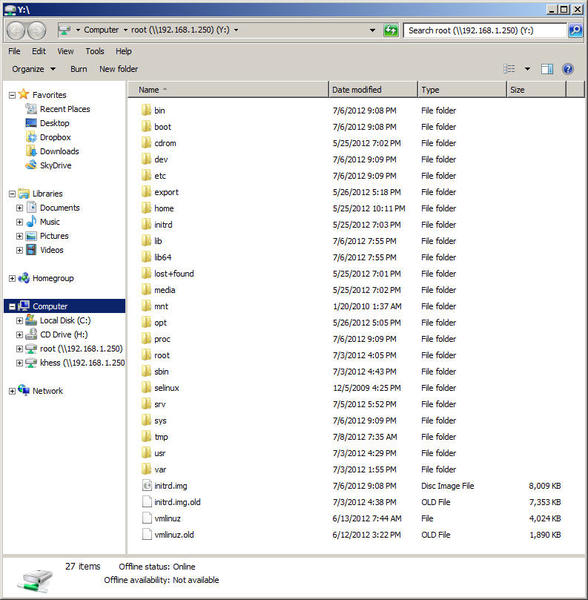
Figure 2 shows, in Windows Explorer format, the entire filesystem on my Linux computer. These directories are at the top level in the filesystem. If this were a Windows computer, this would be the contents of the C: drive.
Each of the top-level directories in Unix has a specific function related to the files it contains. Most of the directories’ functions can be discerned from the name, whereas others are a bit more cryptic in nature and in nomenclature. I’ll explain the directories in more detail in next month’s article, but a few key directories are worth noting here.
The /bin and /sbin directories contain binary executable files for common Unix use and for system maintenance. Device files are located in the /dev directory. As I stated earlier, everything in Unix is a file and devices are addressed via these special device files. For example, on a Linux system, the device file, /dev/hda1 refers to the first partition on the system’s first IDE disk drive. The device file, /dev/hdc or /dev/scd0 refers to the system’s CD/DVD disk drive.
The /etc directory contains critical system files and directories. The password file, passwd , is located in this directory. Don’t be tricked by the spelling of /etc ; the correct pronunciation is “etsy”’ Any directory at any level that contains the word, lib is one that contains library files. The /mnt directory is the traditional temporary mountpoint for remote filesystems. This filesystem mount action is equivalent to mapping a remote drive in Windows.
The /root directory is the root user’s home directory. And, as you might expect, the /tmp directory is where temporary and volatile files reside, like those in C:\Windows\Temp or C:\Temp . The /usr directory is where user-oriented files are located – binaries, libraries, and online documentation – and historically held the user’s home directories. The /var directory holds many system messages, spool files, system mail, logfiles, and more. Because its contents change often, it was named /var for variable. The /lost+found directory is used by the system to recover files during a filesystem check (fsck ). The /opt directory is roughly equivalent to C:\Program Files , where programs such as office suites, some browsers, and other third-party applications install to for general user access.
Several other directories vary from one Unix type to another, and I’ll cover some of those in Part 2, when I return to discuss working at the Unix command line.
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.