Transport Encryption with DANE and DNSSEC
Safe Transport
Communication needs privacy. It forms the basis for confidential and binding exchange. A typical email does not offer any privacy as it passes through the network in cleartext. Anyone who reads the network traffic has full access to the content of the message, so anyone who wants privacy needs encryption. PGP and S/MIME or SSL and STARTTLS are suitable methods for encrypting email. The first two methods encrypt the message; the others encrypt the transport.
Not Always Safe Transport
Transport encryption (Transport Layer Security, TLS) is attractive. It provides a useful level of protection and is transparent to the user. That is good because it saves support costs and allows users to concentrate on the contents of the communication rather than the encryption.
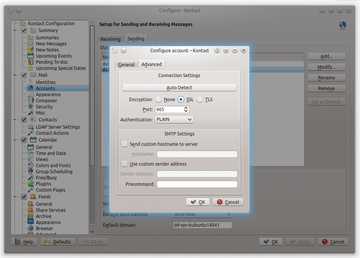
Many admins believe it is sufficient to generate the required certificates for encryption and enable STARTTLS in the SMTP Server and Client (Figure 1). They think that the transport is safe from then on. They are wrong. Transport encryption has some principle-related vulnerabilities, which this article discusses and justifies.
...Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.