« Previous 1 2 3 Next »
Inventory and manage your IT systems
Discovery
Web Interface
After completing installation, it is time to take a look at the software's web interface. To do this, simply type the name of the system on which you ran the installer in your browser followed by open-audit (e.g., http://monitoring.example.com/open-audit/ ) and log in as admin user. The password for the initial login is displayed on the login page.
If you want to test the functions of the Enterprise version now, you can purchase a time-bombed one-year license in the Licenses drop-down. Note that, although you will have access to more functions than in the Community version in this case, the number of manageable devices is limited to 20. In this respect, purchasing this license is really only useful for test purposes. If you require the feature set of the Enterprise Edition, I recommend purchasing a commercial license, which you can import from the Licenses drop-down, as well. A detailed overview of the available functions for each edition of Open-AudIT is shown online [6].
Initial Configuration
Regardless of whether you are using the Community or Enterprise edition, you will want to start by configuring some basic settings, including the email system, which is important for delivery of messages, such as reports from the Open-AudIT discovery processes. You can configure the settings in the Admin | Configuration menu. The Enterprise Edition has more than 160 different configuration options. For an overview of the default settings go to Admin | Configuration | List Configuration .
The next step is to store the credentials for access to your IT assets, which are essential for the discovery process that retrieves information about your devices and for displaying the results in Open-AudIT. The Discover | Credentials | Create Credentials menu item gives you the option of entering access credentials for Simple Network Management Protocol (SNMP), secure shell (SSH), or Windows systems. For SSH-based access, you can of course use SSH keys in addition to passwords (Figure 2). Open-AudIT supports SNMP versions 1, 2, and 3 and uses the Windows Management Instrumentation (WMI) specification to access Windows systems to discover information on the hardware and software in use.
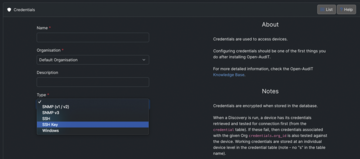 Figure 2: For more extensive system audits, Open-AudIT requires the access credentials for your systems, which are then encrypted and stored in a database.
Figure 2: For more extensive system audits, Open-AudIT requires the access credentials for your systems, which are then encrypted and stored in a database.
Open-AudIT stores the credentials in encrypted form in a MariaDB table named Credentials
. By default, however, the details will be saved in the clear in a JSON or CSV file when the access credentials are exported. This arrangement is not desirable; therefore, you are advised to change the decrypt_credentials configuration parameter from yes to no. Now, when you export the data, it will be in the encrypted form, just as in the database itself.
Network and Active Directory Scans
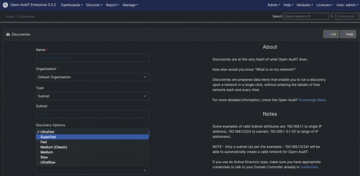
Credentials alone are useless if you cannot also use them as part of a discovery or audit process. At the end of the day, Open-AudIT is essentially about identifying devices on a network and serving up information on them. With Discover | Discoveries | Create Discoveries , you can define different types of network scans. A scan covers a single IP address, an IP range, or an IP subnet.
The type of scan lets you specify the depth of detail with which Open-AudIT investigates a system, which naturally has an effect on how much information is displayed for a particular device (Figure 3). The more detailed a scan, the longer it takes to complete. Creating different scan types for the same network makes sense. For example, one scan could provide a basic overview of the existing systems, and another could provide detailed information on these systems.
If you want to scan the subnets of a Windows domain, Open-AudIT offers the Active Directory scanning type for this purpose. Select this parameter in the Create Discovery menu item and then enter the domain name and a domain controller for this domain. As soon as you start the discovery process, Open-AudIT automatically discovers all the IP subnets that belong to the specified domain and then performs a scan of the systems on these networks. It is important that the WMI ports of your Windows systems be accessible; if not, Open-AudIT cannot collect any detailed information about the systems.
« Previous 1 2 3 Next »
Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.