« Previous 1 2 3
Inventory and manage your IT systems
Discovery
Starting Discoveries
Once you have defined all the discovery processes for your networks, you can access a complete list of options from the Discover | Discoveries | List Discoveries and then launch discoveries directly from this page with the Execute button. The Logs option lets you follow the scan process. The information collected on the devices discovered on a network is then accessible from Details (Figure 4).
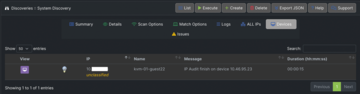 Figure 4: Open-AudIT delivers information for each discovery process and assigns a version number to each set.
Figure 4: Open-AudIT delivers information for each discovery process and assigns a version number to each set.
If the results meet your expectations, you can start the individual discovery processes automatically at specific times by going to Admin | Tasks | Create Task and defining which discovery process you want to run automatically and at what time. Also useful is the ability to create tasks to send different reports, so that, besides viewing the recent reports on the dashboard in the Open-AudIT web interface, you can also mail them, if required. When you define a new task, simply select the Report task type instead of Discovery and define the type of report that you want to mail automatically.
I used the standard administrator account (admin ) for all of the activities tried for this article. Of course, Open-AudIT offers a role-based access model, so you can create additional users and assign specific authorizations to them. To create a new user account, go to Manage | Users | Create Users and assign it the admin role, so the account can handle administrative tasks.
Conclusions
Open-AudIT is a powerful management and information tool for complex networks. In this article, I only scratched the surface, showing you how to install the software and illustrating the initial configuration steps, including creating access credentials and managing the discovery processes, which you can use to scan your networks to glean information on the systems that live there.
If you want to delve deeper into the subject, I recommend a visit to the Open-AudIT support forum [7]. Besides the documentation, you will also find practical articles there to help you implement specific actions. You can use the project's GitHub repository [8] to follow ongoing development of the software or send pull requests to the community.
Infos
- Open-AudIT: https://www.open-audit.org
- FirstWave: https://firstwave.com/products/network-discovery-and-inventory-software/
- NMIS: https://firstwave.com/products/network-management-information-system/
- Nmap network scanner: https://nmap.org
- Visual C runtime: https://learn.microsoft.com/en-us/cpp/windows/latest-supported-vc-redist?view=msvc-170
- Open-AudIT editions:https://www.open-audit.org/about.php
- Open-AudIT community support:https://docs.community.firstwave.com/wiki/spaces/OA/overview
- Open-AudIT GitHub repository:https://github.com/Opmantek/open-audit
« Previous 1 2 3
Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.







