« Previous 1 2 3
BackTrack Linux: The Ultimate Hacker's Arsenal
Examples
Although the BackTrack site offers a long list of tutorials, and you can sign up for hacking classes online with their affiliated Offensive Security site (http://www.offensive-security.com/), the following two examples are good starting places for new security professionals. If you're a system administrator wanting to check a few basic security points on your systems, these two will do it for you.
Zenmap/Nmap
You'll find Zenmap under BackTrack | Information Gathering | Network Analysis | Network Scanners
. Select zenmap
from the list. Refer to Figure 2 from the previous section. Zenmap is the graphical interface for Nmap. If you aren't familiar with Nmap's extensive command list, Zenmap makes Nmap easier by allowing you to make selections via the graphical interface. Nmap is an extremely powerful and complex tool. Its man page is very long and involved. See http://linux.die.net/man/1/nmap for an online version. As an aid to your learning, Zenmap shows the equivalent Nmap command for each sweep you perform.
If you perform the simplest scan of a host (target), Zenmap provides a huge amount of information very quickly. To perform a quick scan of a target, enter its DNS name or IP address into the Target
field, select a scan type (Default: Intense scan) from the dropdown list, and click the Scan
button.
The Nmap command line equivalent of this scan is:
nmap -T4 -A -v 192.168.1.250
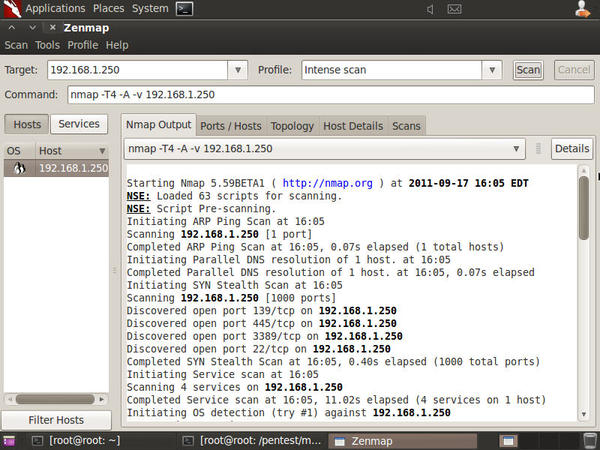
See Figure 3 for a screen shot of Zenmap in action.
You can see from the first part of the scan that Nmap begins with an ARP Ping scan, then a DNS resolution check, then a port sweep to detect and identify open or listening ports, and then it attempts to detect the target's operating system.
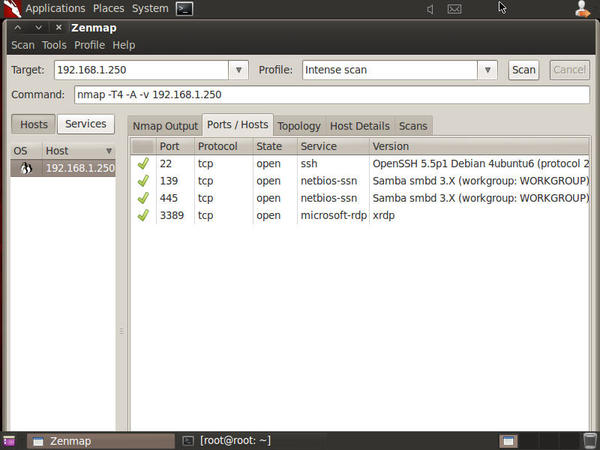
Select a tab to view more detailed information on the scan's results. See Figure 4 for port scan information from the Ports/Hosts
tab.
You'll often see exact version information related to listening services on a host, which helps you determine vulnerabilities and exploitable services.
Nmap is an advanced tool that is widely used among security professionals and hackers. It provides a great deal of information for the least amount of effort. For an exhaustive look at Nmap and Zenmap, I recommend Nmap In The Enterprise: Your Guide to Network Scanning, Syngress Publishing, 2008, Orebaugh and Pinkard. You'll also find a reference guide and other documentation at the Nmap website (http://nmap.org/).
Ncrack
Ncrack is a highly effective and fast network authentication cracking tool. Its purpose is to assist you in identifying user accounts with weak passwords without the hassle of logging into each host and cracking a password hash. Using it, you can check for weak FTP, SSH, TELNET, HTTP(S), POP3(S), SMB, RDP, and VNC passwords.
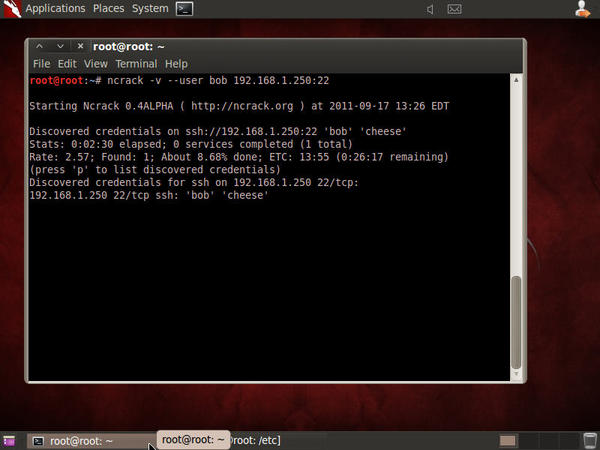
Figure 5 shows what an actual ncrack scan looks like after a successful password crack. The user account, bob
, uses a very weak password: cheese. It took ncrack two minutes thirty seconds to crack this password. This means that a hacker could login to this system using the 'bob' account in less than five minutes and commence working on breaking a privileged account or downloading malware with ease.
System security is serious business, and you should understand the tools that hackers use to compromise your systems. By running your own checks first and strengthening your defenses, you could save your company millions of dollars in losses. Security is everyone's business, and it is your job.
« Previous 1 2 3
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.