Setting up and using Azure Active Directory
Twin Service
Setting up Twitter for the Enterprise
Now I will show how to enable another web application for SSO: Twitter. Unlike Dropbox, a private account is not created for all authorized employees; instead, you need to give several employees access to a shared Twitter account. A Corporate Communications team, for example, needs access to the Twitter account to send tweets to readers. However, Twitter does not have a multiuser system that allows multiple users with different accounts to access the same Twitter channel. I will therefore be using one of the previously mentioned SSO variants: Password Single Sign-On .
The first steps for creating the application in Azure AD are identical to the Dropbox example: Instead of Dropbox, however, you create Twitter as a new application for the directory in the Azure Management portal. Select the Password Single Sign-On option for Configure single sign-on in the overview page. Azure AD then asks which login details it should use when assigning users for Twitter. The login details are stored securely in Azure AD and are off limits to outsiders – even the employees. Next, filter the newly created group AAD_Twitter_Access under Assign Users . Select the group and click Assign in the bottom menu. Azure AD then opens a web dialog when you click I want to enter Twitter credentials to be shared among all my group members . Then, add the username and password for the Twitter account.
This configuration offers several advantages: You can control access to the Twitter channel via membership in a security group. Additionally, you have secured the Twitter account so that none of your employees knows the password. They each log in with their own user account from Active Directory. If an employee leaves the company, you can update the group membership in AAD_Twitter_Access to change the access to the account – without having to change the Twitter account or the password.
Access via MyApps Portal
If employees want to access the Twitter channel, they cannot log in to Twitter themselves – after all, they do not know the password for the channel. Azure AD thus needs to provide a way to handle the login transparently. Part of the Azure offering is the MyApps portal [4], which employees can use to access the applications assigned to them (Figure 9). All applications are stored with a graphic, which then triggers a redirect to the appropriate application when clicked.
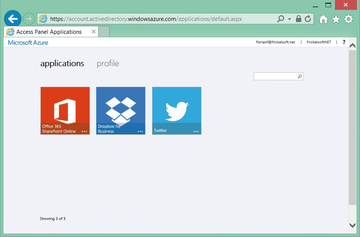 Figure 9: The MyApps portal shows an overview of the applications assigned to the user and provides transparent log ins at the press of a button.
Figure 9: The MyApps portal shows an overview of the applications assigned to the user and provides transparent log ins at the press of a button.
Login transparency is supported by a plugin for the browser, which feeds in the login credentials on accessing the application. Microsoft requests the installation of an MSI package for Internet Explorer when you first click on the application in the MyApps portal. Just installing the plugin is enough for Firefox. Once enabled, single sign-on works over and over for all applications with stored, protected passwords.
Users will find information about their user accounts in Azure AD under the profile tab. Other functions, such as changing AD passwords, are also available there if the Azure AD admin has enabled this.
Multifactor Authentication
Microsoft is currently expanding its online services to include multifactor authentication (MFA). This makes account theft difficult when accessing online resources and also secures access to local applications or to corporate VPNs upon request. Two new offers are particularly interesting for online subscribers: Office 365 customers can enable MFA for all users, as well as Azure and Azure AD customers for their administrative accounts – and for free. Administrator accounts can thus be protected even if Azure AD Premium licenses are scarce or if only an Office 365 subscription is available.
Enabling administrators takes place as follows: First, you enforce MFA for an administrative account. Second, you need to specify your preferences regarding the additional factor when next logging in: Phone, SMS, or unique code through an app, and a cellphone number that Azure MFA will use to make contact. MFA is then enabled for you as an administrator.
You can configure the MFA activation in the directory's user overview. After selecting any directory user, you can then select the Manage Multi-Factor Auth option with the padlock symbol. The portal then switches to the configuration page for MFA. The Enable option appears under Quick Steps when the desired user is selected. MFA is then activated here for the user. A further click on Enforce will enforce MFA.
Only at this point will the user be guided through the wizard upon next logging in. Administrators have to go through the setup once in Enforced mode before they can access the service again. The second factor is always invoked if the first password request and authentication through ADFS were successful.
The second factor is acknowledged via phone functions, such as a call or text message, or via the Multi-Factor Auth app for Windows Phone, iOS, and Android. Users can select their favorite method and configure it. A phone call or a text message are the options for the phone variant – a cellphone number is also stored. The free app can be configured for One-Time Password (OTP) or a push message that has to be accepted. The difference is that cellphone reception is not mandatory for OTP, but it is for the push message.
Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.







