Setting up and using Azure Active Directory
Twin Service
Setting Up SaaS Offers
Microsoft is trying to make the process of setting up federation with cloud software from within Azure AD as easy as possible. Previously, offers such as Salesforce.com had to be federated with the local ADFS infrastructure to support SSO for users. Local federation required setting up manual synchronization of user account data for Salesforce.com, and you had to set up the certificates and SSO settings manually. In the process, Salesforce was established as a relying party in ADFS, and the configuration was monitored and maintained by the ADFS team. Azure AD now handles this task as a service. Federation is set up between Azure AD and the online offerings – the only relaying party you still have to maintain is the one between ADFS and Azure AD (shown in Figure 6 as a light green connection).
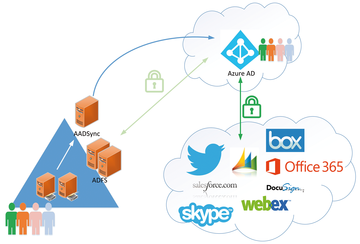 Figure 6: Azure Active Directory serves as a single sign-on platform for additional services from the cloud by different vendors.
Figure 6: Azure Active Directory serves as a single sign-on platform for additional services from the cloud by different vendors.
In this example, I'll show how to set up the Dropbox for Business service. To this end, you need a Dropbox for Business account. A trial version for 14 days will suffice, as long as the "for Business" version is used. For the time being, Dropbox requires you to provide your credit card details to extend the trial version after the 14 days – so you should remember to delete the account on time, if you do not want to continue using the service and just want to test it.
Once you are all sorted with Dropbox for Business, you can configure the first settings in the admin portal. Turn on Enable single sign-on by checking the box below Authentication . This lets you select additional options for fine-tuning. Then, click More about single sign-on below the checkbox to see further details about your Dropbox subscription.
The unique sign-in URL for your subscription assigned by Dropbox is what you are interested in here; in this example it is https://www.dropbox.com/sso/12018794. Save the URL to the clipboard before selecting the Required option for SSO settings. This forces the user to conduct SSO through the Azure AD – there are no passwords for Dropbox to store for your users. Do not worry; administrative users can still log in to Dropbox if the Azure AD or their local ADFS are unavailable at any point.
Adding an Online Service
Next, I'll address how to set up Dropbox SSO via the Azure AD portal. To this end, you'll need to log in to the Global Azure Management portal as a global administrator. You will see all the registered directories under Active Directory . Select your directory and then choose the Applications in the top menu. There you will find a list of all registered applications. If you use the directory for Office 365, Exchange Online and SharePoint Online will appear there as the first two applications. Clicking Add in the bottom menu will launch the wizard for new applications. Next, confirm to Azure AD that you want to continue to Add an application from the gallery .
The gallery is familiar with more than 2,400 applications, which are grouped into various categories. Type Dropbox as a search term in the top-right search field; Dropbox for Business will then be suggested. Clicking the confirmation button will create the basic framework for federation in your Azure AD. The Azure portal jumps to the application overview page. You can always return to this overview if you select the appropriate directory in the Azure portal via Active Directory and then Applications and click on the desired application. The following overview shows three steps that are required for the single sign-on relationship:
- Enable SSO.
- Enable automatic user provisioning for Dropbox.
- Grant permission for individual users to use Dropbox.
Click on step 1 (Configure single sign-on ) to open the wizard. The connection between Dropbox and the Azure AD can be set up in three ways – all of them named SSO. Select Windows Azure AD Single Sign-On for purposes of this example and continue to the next step of the wizard. The other two options are for different scenarios.
The second option, Password Single Sign-On , allows Azure AD to store login data, which is sent transparently to the target application when a user logs on. I will use this option later with Twitter. The Existing Single Sign-On option takes you to a setup for federating with the local ADFS farm. Although this option also leads to a SSO relationship to Dropbox, you would lose some of the benefits of Azure AD: automatic user provisioning in the cloud application, monitoring of the federation relationship, and Azure AD as a central SSO interface.
The second page of the wizard now requires the Dropbox sign-on URL. Here you can add the URL that you copied from the Dropbox administration page – Azure AD wants the complete URL: https://www.dropbox.com/sso/12018794. You receive two last, important pieces of information on page 3: the actual sign-in URL for Azure AD and a certificate used to create the federation relationship.
Next, copy the sign-in URL for Azure AD, which typically starts with https://login.windows.net into the clipboard (Figure 7). Then, download the certificate offered. I will be using both the URL and the certificate to set up Dropbox: Add the sign-in URL for Azure AD back in the Dropbox admin portal. Upload the certificate .cer file to Dropbox in the same step. This completes the configuration of Dropbox. At this point, you need to finish the wizard in Azure AD. Confirm the checkbox in the third step and finish the wizard. The checkbox instructs Azure AD to release the downloaded certificate for Dropbox. Otherwise, the certificate would remain "pending" and not be released.
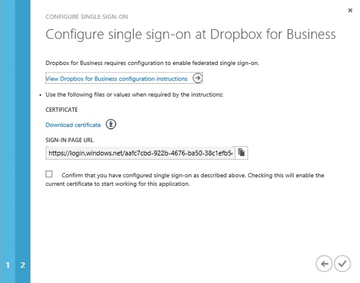 Figure 7: The login URLs and a certificate need to be replaced for federating applications with Azure AD.
Figure 7: The login URLs and a certificate need to be replaced for federating applications with Azure AD.
The second step takes place below the Configure user provisioning item. The wizard lets you provision users in a single step. You are now granting Azure AD permission to create, modify, and delete users in Dropbox. Clicking Enable user provisioning will open a new Dropbox window that asks for the authorization from Azure AD. If you are no longer logged in to Dropbox, you will be prompted to log in again.
The third step is called Assign users : The button changes to the Users and Groups overview for the application. From here, the users and, possibly, the groups are enabled for the application. Apart from individual test users, you should only allow groups to use the application to keep things manageable.
The view in Azure Active Directory Premium is different from the normal view. The overview shows a filter option for users and groups if you have licensed Azure AD Premium (even as a trial). You can select users and groups and assign them to the application. You can only assign users if you do not have Azure AD Premium. If you do have Azure AD Premium but can still only see users in the overview, you need to assign your administrator a Premium license: Select your directory in the Active Directory section of the Azure portal and switch to Licenses in the top menu. You can assign a new license in the license overview via Assign . If you have a particularly large number of users in the directory, select the search filter in the top-right corner of the table by clicking on the magnifying glass icon.
Testing SSO
Azure AD provisions new users cyclically in federated applications. The newly assigned users should appear under Dropbox for Business after a maximum of 15 minutes (Figure 8). Provisioning is handled by Azure AD and ends with creating or deleting a user account in the respective application. Any further steps for creating the SSO feature are controlled by the SaaS application.
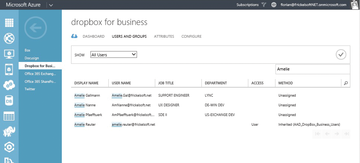 Figure 8: Access to SaaS offerings is controlled centrally and assigned either directly to users or via membership in access groups.
Figure 8: Access to SaaS offerings is controlled centrally and assigned either directly to users or via membership in access groups.
Provisioned users in Dropbox for Business will receive a Welcome email in which they need to enable their Dropbox account before SSO will start to work. The email contains the name of the company, the Dropbox project to which the user is invited, and a link for activation. Single sign-on is possible for users after activation. They must enter their username on the login screen and are then authenticated by ADFS. SSO thus works without users' needing to enter their password again.
Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.







