« Previous 1 2 3 4 Next »
Delegate and restrict authorizations in Azure AD
Temporary Admin
Dynamic AUs
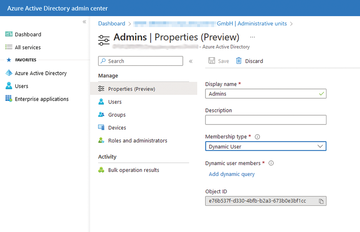
Dynamic AUs support queries for membership in an administrative unit on the basis of user and device attributes. Therefore, membership can be automated to a large extent. When you click on a management entity in the Azure portal, you can customize its settings and assignments (Figure 4). Besides an Assigned membership type, you can also choose between Dynamic User and Dynamic Device in the Properties pane.
After setting up an administrative unit with dynamic membership, the Add dynamic query link lets you define your own rules for membership. You can also access the attributes of the user accounts or devices. Once you have defined and saved the rule, you can view the members on the main page of the AU and access the objects. You can also configure a membership rule at this point.
Configuration with PowerShell
Administrative units are not a complex product. So that they can contribute to improved security in Azure AD, you need to configure the rest of the environment to allow the management entities to achieve their full potential, which includes managing Azure and the AUs in PowerShell. To manage administrative units in PowerShell, use the cmdlet
New-AzureADMSAdministrativeUnit -Description "West Coast region" -DisplayName "West Coast"
Before you can work with PowerShell in Azure, you first need to do some preparatory work. Almost all areas in Azure AD can be managed with PowerShell, too, not just the administrative units. Besides managing Azure with the Azure Cloud Shell, you can install the module for managing Azure AD in PowerShell, which lets you administer sections of Azure AD locally and, incidentally, parallel to managing Active Directory. To begin, install the Azure AD PowerShell module on your computer and open a connection to Azure AD with
install-module azuread Connect-AzureAD
To view all of the cmdlets for Azure AD management, use
get-command -module azuread
For example, you can display the commands for managing administrative units by running the cmdlet
Get-Command *AzureAD*AdministrativeUnit*
When assigning administrative units to specific users or groups, user logons should be monitored. This also applies to the admin accounts that are members of the administrative units. Changing memberships often requires a new registration at the AAD. Whether this login was successful can be monitored in the Azure portal.
When assigning administrative units to specific users or groups, as well as to admin accounts that are members of the administrative units, you need to monitor user logins. When changing memberships, it is often necessary to re-register with Azure AD. You can use the Azure portal to discover whether the login worked. In the Azure AD admin center, click Users | <user> | Sign-in logs to check when users have logged in and where. The portal also displays the IP address from which the login took place and the use of multifactor authentication. Multiple unsuccessful logins indicate an attack on a user account.
If you type Get-AzureADUser in the Azure Cloud Shell or Azure PowerShell, you can view information about the user accounts in an Azure subscription. If you want to see more detailed information about a user or group in Azure AD, use the cmdlet with the ObjectID parameter
Get-AzureADUser -ObjectID 3b47a729-16c1-4be1-9ee2-7f3bd00a346b
You can retrieve the ObjectID for each user after entering Get-AzureADUser, and you can use UserPrincipalName, typically the email address the user uses to log in, as the ObjectID. To view all the data for a user account, pass the results from Get-AzureADUser to the select cmdlet and use the * wildcard to output all the data:
Get-AzureADUser -ObjectID 3b47a729-16c1-4be1-9ee2-7f3bd00a346b |select *
Administrative units can also be mapped to groups that you manage in PowerShell, as well (e.g., to supervise administrative tasks). The individual groups in Azure AD can be displayed with the Get-AzureADGroup cmdlet. Additionally, you can create new groups, control group memberships, delete groups, and much more in PowerShell. To retrieve all the cmdlets, use
Get-Command *ADGroup*
User accounts that are members of an administrative role can manage a group. In turn, the role can be associated with an administrative unit to which the group has been assigned.
DIY Administrative Tasks
After assigning admins to administrative units and associating these AUs with users, groups, and devices in Azure AD, admins in the AU can also perform various tasks to manage the objects. However, users can also perform many tasks themselves given sufficient authorization. The focus of the AUs is on delegating tasks for managing the linked objects.
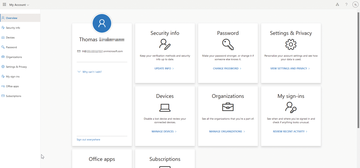
Azure AD provides a self-service portal where all users can log in to manage their own user accounts (Figure 5). If users also have a Microsoft account, it can be found on a separate portal. Both accounts can be accessed as shown in Table 1 under User Portal. Users can change or reset their passwords, for example, and also adjust settings and optimize data protection. You can also review your own logins here (e.g., to discover whether an account has been hacked). If Microsoft Office licenses are on file for an account, users can also download the installation files through the portal. Administrative units are not mandatory for this action.
« Previous 1 2 3 4 Next »
Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.