« Previous 1 2 3 4 Next »
Remote access with Tactical RMM
Spy Story
Adding Hosts
The best RMM environment is useless if it does not contain hosts that it can manage further down the line. Logically, the next step is to install the necessary agents on those systems. Again, a couple of details need to be considered, but these details are specific to the operating system.
If you assume the statistics regularly published on the Internet for the distribution of desktop operating systems are roughly correct, the majority of systems managed in the wild probably use Windows. On the one hand, this is good news, because the Tactical RMM Windows agent offers a number of features that are not available for the Linux and macOS agents, including, for example, the option to check the current patch status of the system remotely (Figure 2). On the other hand, the Tactical RMM agent setup on Windows is a little quirky.
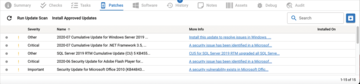 Figure 2: Tactical RMM offers comprehensive reporting mechanisms, such as an overview of the patches installed on a Windows host. Actions can also be planned on the basis of this information.
Figure 2: Tactical RMM offers comprehensive reporting mechanisms, such as an overview of the patches installed on a Windows host. Actions can also be planned on the basis of this information.
Signed Agents Cash Only
One issue is having to cope with comprehensive antivirus (AV) protection under Windows, which is normally helpful because it ensures that the system is protected against classic viral attacks from the web. Unfortunately, antivirus software clashes with Tactical RMM because it is supposed to be able to execute its code on the system and even take control of the system for remote maintenance. From the point of view of antivirus software, Tactical RMM or its agent looks exactly like a virus.
To avoid problems, you need to stick to a couple of guidelines. First and foremost, you should use the digitally signed packages to install the Tactical agent [3]. Unlike their unsigned counterparts, however, these packages are only available if the organization running the Tactical RMM installation sponsors the project [4]. It is important to understand that signed agents are not available as part of the generic packages. Instead, Tactical RMM dynamically generates an installation package for each host you want to add and deploys this package on the target system. The digital signature is tied to sponsorship of the project.
If you need signed agents, which is true for most corporate users, you must sign up for at least the Tier 1 sponsorship level, which will set you back $55 a month; in a corporate context, this kind of expenditure will typically be manageable, especially given that, according to Tactical RMM, up to 200 target devices can be monitored in a meaningful way in this sponsorship tier.
Exceptions for Antivirus Software
Besides installing the signed agents, you also need to make sure you define an exception for the Tactical RMM agent binary in your antivirus program (i.e., you must explicitly tell your antivirus software that RMM is not a virus but is permitted to execute code on the target system). If you use Windows Defender, the default AV tool on Windows, you can do so in PowerShell:
Add-MpPreference -ExclusionPath "C:\Program Files\Mesh Agent\*" Add-MpPreference -ExclusionPath "C:\Program Files\TacticalAgent\*" Add-MpPreference -ExclusionPath "C:\ProgramData\TacticalRMM\*" Add-MpPreference -ExclusionPath "%TEMPDIR%\is-*.tmp\tacticalagent*"
Once you have completed these preparations, the rest of the agent install process is uncomplicated. Now the agent deployment for the Default site mentioned previously enters the scene. To set the ball rolling, click Agents | Manage Deployments and New . As a rule, you will want to keep the default settings. The new deployment will then appear in the list along with a Copy Link button. Copy the link and call it up in the browser on the target system.
The signed agent package then begins to download. Double-click to trigger the installation of the preconfigured agent, which automatically contacts the issuing Tactical RMM instance once the process has completed. The device user can handle this step if you do not have direct access to the device. Of course, this requires cooperation on the part of the user.
« Previous 1 2 3 4 Next »
Buy this article as PDF
(incl. VAT)
Buy ADMIN Magazine
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Most Popular
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you've found an article to be beneficial.







